
The world of business has changed dramatically over the past few years.
Today, it’s more digital and connected than ever, leaving security and technology teams stretched even thinner. Privacy and data regulations are increasing on a state and national level; threat actors are learning and evolving; and cybersecurity has finally become a boardroom priority!
Now that you have leadership’s attention — what will you do? If your answer is “GRC as usual,” it may hold you back.
What Is “GRC as Usual”?
Traditional GRC approaches made a lot of promises (most of them unfulfilled!). To demonstrate, let’s begin by defining GRC.
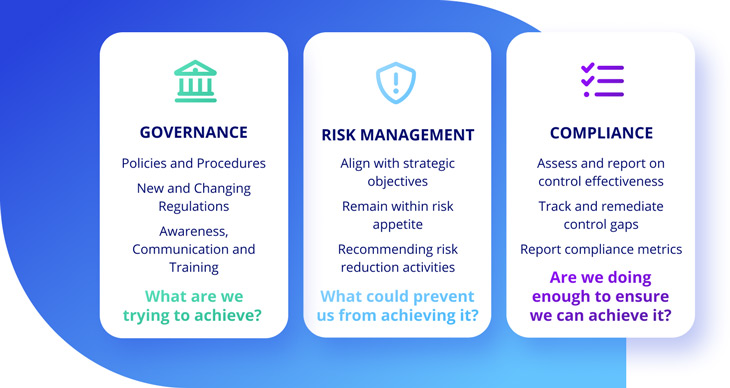
Governance
The governance team creates, maintains and communicates policies across the organization. They monitor and manage changes in regulations or requirements. And they communicate and provide security training to the organization. They ask “What are we trying to achieve?”
Risk Management
The risk management team ensures that business decisions and actions remain within their risk appetite. They ensure acceptable levels of risk aligned with strategic objectives and recommend risk reduction activities accordingly. They ask the question “What could prevent us from meeting our objectives?”
Security
The cybersecurity team, which traditionally is not part of GRC, implements the recommended or prescribed security mechanisms to reduce the risk to the organization.
Compliance
The compliance team tests and reports on the effectiveness of those security mechanisms. They will track remediation efforts and aid in risk reduction. They ask “Are we doing enough to ensure we can meet our goals?”
3 Broken Promises of “GRC as Usual”
Now let’s talk about what we were told GRC could do for us. Do any of these sound familiar?
- You can effectively govern your risk landscape
- You can make better-informed risk decisions
- Your compliance with regulations will keep you secure
You’ll notice that nowhere does it say you can assess…
- What you are trying to achieve
- What could prevent you from achieving it
- If you are doing enough to ensure you can meet it
Without that, these are just broken promises.
Promise #1. You Can Effectively Govern Your Risk Landscape
Creating a single source of truth for security and compliance information is critical, but the silos of security, governance, risk and compliance teams often inhibit collaboration and reduce risk visibility.
Further, traditional GRC doesn’t consider the business context or financial impact of risk and compliance. You can’t see risk in the context of what matters to the organization or ensure proper prioritization and investment without a scalable unified risk program centered around unique business priorities.
This level of transparency empowers business leaders to invest and prioritize risk treatment options.
Promise #2. You Can Make Better-Informed Risk Decisions
We recently conducted a survey of 261 information security, governance, risk and compliance respondents within the United States. One of the outcomes was a clear lack of understanding and consistency around fundamental risk terminology. Less than half of the respondents defined risk or threats the same way.
This isn’t all that surprising.
The traditional first step in managing risks is identifying them. However, “risk” is often a blanket term for anything adversely associated with the organization. Thus, risk registers get filled with items that aren’t truly risks. And when everything is a risk, it can be difficult to know what needs to be fixed.
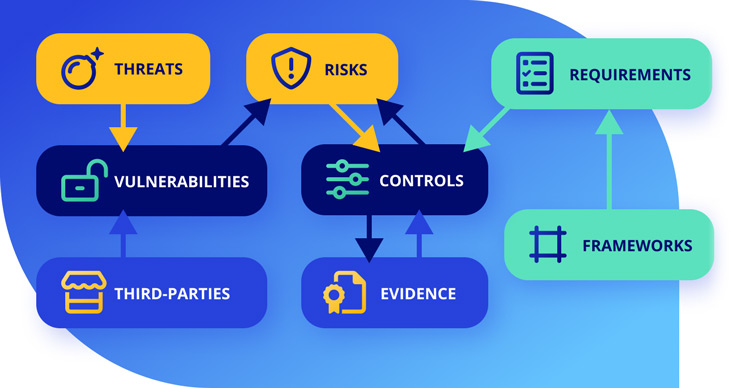
Organizations are often blind to the interconnectivity of threats, vulnerabilities, risks and controls.
The Key to Quantifiable Risk Assessments
However, each is an essential piece of risk management.
Your risk dynamically adjusts as…
- Threats change
- Vulnerabilities are added or remediated (including third-party relationships!)
- Control implementations are assessed
Leveraging those relationships — and each object’s impact on the others — fosters quantifiable risk assessments.
Promise #3. Your Compliance with Regulations Will Keep You Secure
An oversized focus on compliance and satisfying requirements is not well-suited to the growing interconnectedness of risk across an evolving digital business.
Many began automating the collection of evidence to streamline audit preparation. However, putting your compliance program on “auto-pilot” perpetuates the concept that compliance equals security. But just because you’re compliant doesn’t mean the risk is sufficiently controlled.
A different approach is needed to reduce manual processes without relying on point-in-time compliance activities or potentially deceptive assessment processes.
How to Make GRC Deliver on Its Promises (& More)
So, how can you finally realize the promise of GRC — plus align your program around your company’s strategic business priorities?
Step 1: Bring Your GRC Program Up to Speed
Your first step? Shift to scalable, quantifiable and always-on risk management.
Here’s how…
View Your Risk in the Context of Business Priorities
Business leaders need to understand cyber risk and how it impacts the business, so they can make informed decisions on security investments.
By creating optics defined by business priorities (such as product, business unit or operating region), the RiskOptics ROAR Platform enables a tailored view of risk in the context of your business. Optics allow you to view the different areas within your business and quickly identify where you should focus your attention.
Quantify Your Risk with Hard Numbers
To quantify and communicate risk, a unified methodology that leverages the security and compliance activities already being done within an organization is needed.
Relying on qualitative scores — such as High/Red, Moderate/Yellow and Low/Green — disguises the risks’ true impact and likelihood.
Qualitative risk assessments can’t accurately measure an organization’s susceptibility to a cyberattack or how much it will cost the company to secure itself better.
When the impact and likelihood of threats and vulnerabilities are combined with controls’ weight, maturity and effectiveness — inherent and residual risks automatically change to reflect the most up-to-date risk score. Aligning this with the financial impact on the organization increases visibility into the value of security investments.
Switch to Always-On Risk Management
Just as qualitative risk assessments can inadvertently downplay risks — risk heatmaps and point-in-time dashboards can present misleading information. Heatmaps provide a view into risk, but you can’t see the whole picture without details on how risks change over time and the factors that led to the change.
ROAR establishes scalable, quantifiable and always-on risk management that helps Risk Insiders quantify and communicate risk in the context of their business. Schedule your FREE demo to see it in action today!
Step 2: Get the NEW Strategy for a Winning Security Program
Let our Risk Insiders show you the new strategy for building a winning security program this year — and beyond! Watch our recent expert session to discover how to convert risk into your strategic business advantage, plus…
- Take your program further with fewer resources
- Regain board confidence (and secure future funding)
- Make squashing risk a cinch with ROAR’s new capabilities
Up your GRC game in just 59 minutes. WATCH NOW.




