In the realm of information security, risk management is often regarded as a vital component in safeguarding organizations against cyber threats. However, despite the efforts of security personnel and the existence of risk management systems, many organizations continue to encounter issues.
It is crucial to acknowledge that the clunkiness of information security risk management – and the subsequent misunderstandings – can be major obstacles to achieving effective risk mitigation.
In this blog post, we explore the complexities of cyber risk and shed light on the misunderstandings that can impede progress in information security risk management.
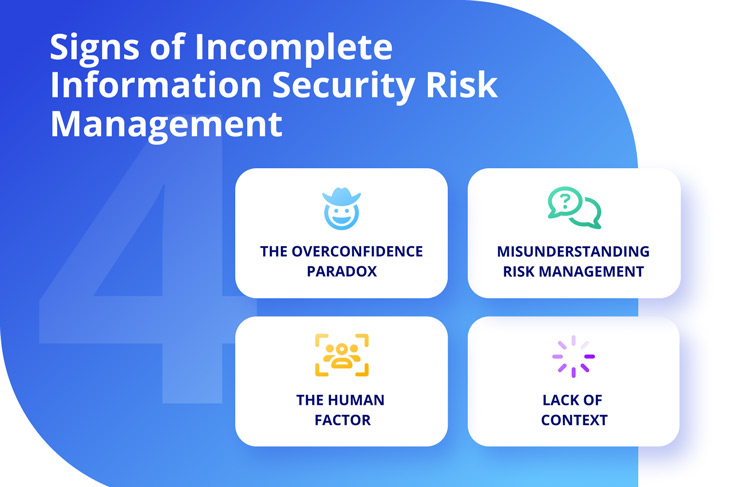
4 Indicators of Incomplete Information Security Risk Management
Confident you have the right elements in place for effective information security risk management, yet still find staying ahead of cyber risk or securing board buy-in challenging? This could indicate gaps in your strategy.
Below are 4 of the most common ones.
#1. The Overconfidence Paradox
One of the primary challenges in information security risk management is the overconfidence that often arises from having a risk management system in place. However, the “something is better than nothing” mentality fosters a false sense of security that their system is foolproof.
It is essential to recognize that cyber risk is multifaceted and continuously evolving. Relying on the existence of a risk management system without understanding its limitations and intricacies can lead to blind spots and vulnerabilities that threat actors can exploit.
#2. Misunderstanding Risk Management
Another significant issue stems from the misunderstandings surrounding risk management itself. Risk is often mistakenly equated with a realized vulnerability or the likelihood of a threat materializing.
While these elements are an important aspect, true risk management leverages the relationships between each element to provide a broader perspective. It involves identifying and understanding potential threats and realized vulnerabilities, evaluating their potential impact on your business and implementing appropriate measures to mitigate them.
Neglecting any of these steps can result in an incomplete risk management strategy.
#3. The Human Factor
Human factors also contribute to the challenges of information security risk management. Often, security personnel focus primarily on technical solutions and neglect the human element. This oversight can lead to inadequate training, poor security awareness and a lack of understanding among employees regarding their roles and responsibilities in maintaining a secure environment.
Cyber attackers often exploit human vulnerabilities through tactics like social engineering, making it crucial to address this aspect comprehensively in risk management efforts.
#4. Lack of Context
Risk is usually communicated without context, further muddying the waters. Despite the C-suite and the board of directors getting more involved in signing off on cyber risks and information security spending, they tend not to truly understand how the risks and threats presented affect the business. This, in turn, leads to poor decision-making and ineffective allocation of resources.
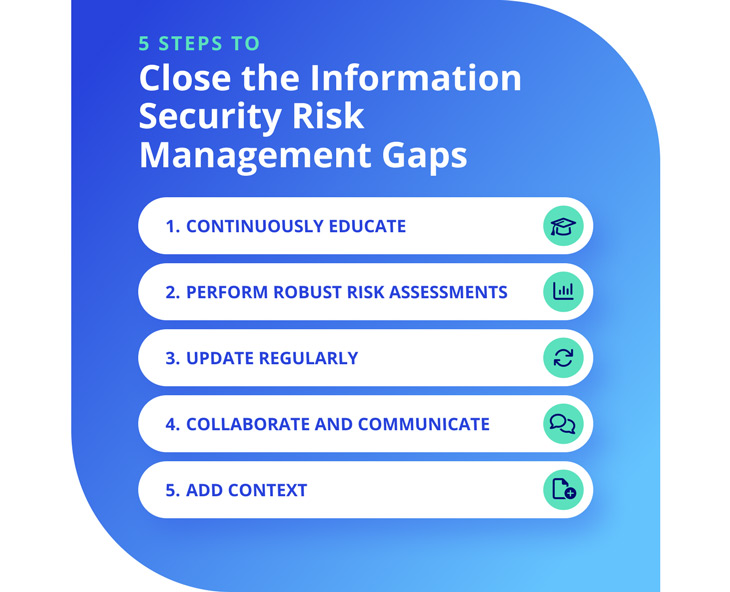
5 Steps to Close Information Security Risk Management Gaps
To overcome the clunkiness and misunderstandings in information security risk management, organizations must adopt a holistic and proactive approach.
Here are 5 key steps to consider:
Step #1. Continuously Educate and Raise Awareness
Invest in ongoing education and training programs to enhance the knowledge and security awareness of employees regarding cyber risks and their roles in mitigating them.
Step #2. Perform Robust Risk Assessments
Conduct comprehensive risk assessments that go beyond technical vulnerabilities, considering factors like human behavior, threat intelligence and business impact.
Step #3. Review and Update Regularly
Continually review and update risk management strategies to align with the evolving threat landscape and organizational changes.
Step #4. Collaborate and Communicate
Foster collaboration between security teams and other departments, emphasizing effective communication to ensure a unified understanding of cyber risks and risk management measures.
Step #5. Add Context
Risk management must be communicated in the context of your organization. Understand the importance of the business group, product or geography to the business, and use that to help executives understand the true risk and return on investment of remediating.
Recognizing the limitations of existing systems, addressing the human factor and embracing a holistic approach are crucial steps towards improving risk management effectiveness. By doing so, organizations can better navigate the complexities of cyber risk, bolster their security posture and protect themselves against the ever-evolving threat landscape.
How Common Is Incomplete Information Security Risk Management?
Information security risk management can be challenging, plagued by complexity, misconceptions and contradictions. And incomplete strategies are quite common.
In fact, Researchscape and RiskOptics’ new survey of more than 260 security, compliance and risk management professionals found that many feel confident in their programs, yet still cite staying ahead of the increasing quantity and severity of cyber threats as their top challenge.
What are other common gaps in information security risk management programs? Explore the research findings in this free report. Download now.