
I think it’s fair to say that as your company grows, you will likely need to engage with outside parties to supplement or outsource elements of your business. This may include vendors and suppliers, contractors or service providers. Engaging with third parties has a lot of benefits, but it also comes with challenges. Mainly, you can outsource the work but not the risk. Partnering with third parties exposes you to higher levels of risk because in many cases you give up control over the work, how it is done and how it is secured. You must rely on the third party to put sufficient measures in place to reduce the risk to your acceptable level.
If you’re an avid reader of the RiskOptics blogs, and I hope that you are, you may have had some strong emotions in response to our recent post Making the Shift From Vendor Risk Management to Third-Party Risk Management. I received a lot of feedback. Some folks reached out to thank me and some folks reached out to tell me I’m crazy. But overwhelmingly, people reached out to ask me for help. Most of you recognize the need and the value behind data-driven and continuous monitoring of third-party risk but struggle to identify ways to put the concepts into practice.
So here’s 5 steps you can take toward a better third-party risk management program!
-
Implement a Centralized View of Third Parties
This may seem like an easy first step but without the right stakeholders engaged, it can be difficult. Traditionally, the different types of third parties are managed by different teams and often have different vetting and monitoring processes. This can make it difficult to capture a centralized view of third-party risk.
You might also need to consider third-party relationships with merging companies, acquisitions and partnerships. Each of your third parties will also have a series of third parties (that we can call fourth parties) that may also impact you. As you can see, the list of external providers keeps growing and growing.
While most companies might have a vendor register, your first step should be to expand your centralized inventory to include all third party relationships as well as any critical fourth-party relations. This is key to the success of the next steps.
-
Update Your Due Diligence Processes
We can all agree that simply engaging with third parties opens us up to risk. But I’m going to take it a step further and say that the way we manage third parties also opens us up to risk, maybe even more so than the third parties themselves.
For most of us, we have a third-party management process that looks something like this.
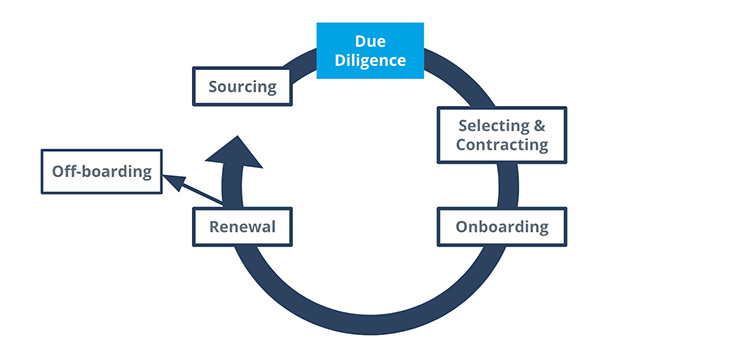
The business requests a new third party, you conduct a security review, contracting and onboarding is done and a reassessment is done at the annual contract renewal. Generally speaking the various phases involve multiple departments such as procurement, legal, IT etc.
And while this process has worked well in the past there is one large weakness here … it’s based on a point in time risk identification process. And this is a problem. It’s time to go beyond annual security assessments to a model of data driven visibility into your third-party risk. This involves establishing a baseline and automated mechanisms to alert on deviations. So you don’t have to wait until the next contract renewal to reassess because you’ll have continuous visibility into the level of risk associated with your providers.
-
Align with Business Priorities
Knowing which external providers pose the most risk to your business is key to a successful third-party risk management program. To begin, you need to first understand your business and your objectives. What are the “big things” your company cares about? For many of you the answer will likely be some combination of data privacy, infrastructure security, sales operations and application security. All of these things are important to the success of your organization. Thinking in these terms, you can now “assign” third parties to your programs, visualize which impact your most critical areas and tailor your assessment processes to be commensurate with the level or risk.
Traditional methods assume that all providers impact all organizational processes in the same way, and that simply isn’t true. Even though two providers have the same level of RISK doesn’t mean they will have the same level of IMPACT on your business. And if you aren’t using programs centralized around your business objectives, then you have no real way of knowing how each provider impacts your ability to meet your goals.
Instead of viewing and assessing external providers according to a generic questionnaire, we are going to start with business initiative first and assess which third parties will impact it. Approaching third-party risk this way helps you effectively communicate and discuss risk with your stakeholders because you are talking in their language about their priorities to help accelerate them while protecting your organization.
As an example, you have two providers that offer hosting services to you. Using your standard risk assessment methods you determine that both of them are high-risk. In this case, both are weighted equally. However, consider that one provider hosts your website (provider A) and the other hosts your customer information databases (provider B). In this case, Provider B has a direct impact on your organization’s ability to maintain data privacy which in turn has a direct impact on your revenue stream. Provider B is a lot more critical.
Being able to identify the highest impact providers enables you to focus your remediation activities to reduce the risk to your most critical programs.
-
Be Proactive
Earlier I mentioned the need to go beyond annual assessments to a model of data driven continuous visibility into your third parties. If you think about why we conduct third-party assessments, we are looking for indicators of risk associated with each provider. But traditional TPRM processes only look for those indicators at a point in time.
We recommend utilizing independent security tools to collect information related to the provider’s security posture. There are several options for collecting risk data that range from technical indicators (like botnet infections and expired certificates) to reputational risks (like leaked credentials and hacker chatter). Skeptics may question the reliability of this information as it is collected from public sources. To them I say, first, the accuracy is on par if not higher than some questionnaires you may receive. And second, these services are meant to be indicators of risk. A “check engine light” for third parties to alert you that something might be wrong. There may be some false positives. But isn’t that better than not knowing about the actual positives?
Consider for a moment a video doorbell. It is configured to record and alert when there is motion sensed. Sometimes that motion is a bird or my kids riding their bikes. But sometimes that motion is a solicitor or a potential threat. Isn’t it better to be alerted to false positives than not know when there is a real threat?
By automating the ingestion of this data, you can identify the provider’s likelihood of causing you harm or preventing you from meeting your business objectives. It also enables you to establish a baseline and mechanisms to identify deviations. Now you don’t have to wait until the next contract renewal to reassess because you’ll have continuous visibility into the level of risk associated with your providers.
When you combine this data-driven model with the visibility of which business objectives the provider impacts, you’re able to quickly identify the most critical providers and focus your efforts on mitigating controls. You’re now enabled to make proactive and targeted action to better safeguard your company and reduce risk more effectively.
-
Identify and Prioritize Gaps With Highest Yield
Having used security scores to prioritize your highest risk and highest impact third parties, you’re now able to collect evidence and document compensating controls from your most critical providers. Consider aligning your third-party risk management program with your compliance requirements. By doing so, you’re able to assign evidence requests to the vendor that map to your organization’s controls and assess their documentation in the same manner you would your own. The control efficacy directly impacts the provider’s residual risk score thus enabling you to quickly and easily visualize the third parties furthest from your target risk appetite.
Further, because the information is brought in through integrations and updated as new information is available, you gain more continuous oversight of your providers. If the risk score goes above your risk appetite, initiate a new assessment and collect new evidence!
Continuous monitoring helps you stay ahead of threats by alerting you to changes in your third-, fourth- and fifth-level suppliers, partners, vendors and other third parties so you can take preventative action.
Interested in learning more?
Watch our recorded webinar, “Close the Back Door! 5 Ways to Reduce Third-Party Risk”, where RiskOptics experts share and discuss:
- Why third-party relationships introduce high risk to your organization
- Key considerations to better identify, manage and mitigate third party risk
- How cybersecurity risk ratings can complement your risk mitigation efforts
Gain a clear understanding of the steps you can take to better avoid, manage and mitigate third-party risk to protect your operations, reputation and revenue.




