
It’s been almost a year and a half since I hung up my GRC manager hat and joined the RiskOptics Technical Product Management team. And while there are certain areas of that job I don’t miss (2 AM incident response, for one), there are plenty of things I do miss about my time as a security practitioner…
Winning at Risk Management with ZenGRC
In the GRC world, seeing the output of your work directly reducing the risk to your business fosters a sense of satisfaction that is hard to replicate.
I recently had the opportunity to discuss the use of ZenGRC with several customers and was thrilled to be back in those shoes – assisting our customers in building healthy, scalable GRC processes designed to measure and communicate risk reduction. And the comment I hear most often is, “There’s something for everyone in ZenGRC!”
If you haven’t had a chance to explore ZenGRC, you might not realize just how much it can revolutionize your GRC program.
So, let’s walk through a day in the life of a fictional GRC team to see how ZenGRC can transform disjointed and siloed processes and enable the governance, compliance and risk managers to collaborate as a team of Risk Champions, surfacing unseen risk and converting it into a business advantage.
Automated Governance
Gary is the governance manager at Panda Partners. His job is to manage the sets of policies, standards and frameworks that the company uses to achieve its business goals. At Panda Partners, governance is a subset of compliance and doesn’t include formal workflows or processes to monitor for changes and iterate accordingly.
Wouldn’t it be great if there was an automated way to maintain governance?
Well, the RiskOptics ZenGRC does just that!
- Out-of-the-box content spanning the most common security and privacy regulations and standards linked together by backend mappings.
- Centralized repository of business objects: the policies, processes, services and roles necessary to implement controls.
- Ability to add an expiration date to each object to ensure they are reviewed, updated and approved at regular intervals.
- Instant gap analysis functionality.
Instant Gap Analysis:
Panda Partners has an ISO27001:2013 framework monitor with control implementations mapped to all in-scope requirements. The compliance team has been collecting and assessing evidence for some time now and 100% of the requirements have effective controls.
One day, Gary’s boss asked him, “What will it take to meet the ISO27001:2022 requirements?”
Because ZenGRC backend mapping links similar requirements together, when frameworks change or a new framework is released, ZenGRC automation produces an instant gap analysis. Gary simply created a new framework monitor for the updated version, and ZenGRC identified the overlap and necessary areas requiring action.
Automated Evidence Collection and Assessment
Gary works closely with Conner, the compliance manager. Conner felt like the most hated employee at Panda Partners. Whether doing an internal assessment or prepping for an external audit – he was always asking people for evidence.
Over lunch one day, Connor was lamenting that bribing the IT team with donuts wasn’t working anymore. He needed a better way to collect evidence but he was confused by all of the options on the market.
Once back at the office, Gary showed Connor ZenGRC connector’s functionality.
Collect Evidence YOUR Way
Collecting evidence directly from the source is extremely valuable, but is insufficient alone. Connor was thrilled to see that ZenGRC has four ways of capturing evidence:
- Attach it yourself.
- Request it from a ZenGRC user.
- Request it via an external ticketing system (such as Jira or ServiceNow).
- Automated collection directly from the source.
This flexibility enables a holistic approach and significantly reduces manual tracking and reminders.
Assess and Remediate Faster:
As Conner began enabling connectors, he quickly unlocked the power of automated assessment, as well. For many requirements, ZenGRC knows the desired outcome and can assess and report if that outcome is not met.
This functionality was tested when Conner was out on vacation. An automated evidence assessment found that one of the AWS accounts had a root user that was enabled. ZenGRC assessed this as an ineffective control, and a new task could be assigned to the owner to start remediation. The issue was fixed before Conner returned to the office.
Connecting Risk and Compliance
Panda Partners recently hired Risk Manager Regina. Along with Gary and Conner, she reports to the CISO, Scott. At their regular monthly meeting, Scott was impressed with the reporting and dashboards Conner provided. He could clearly see what frameworks had ineffective control implementations and what issues or tasks were open for addressing them.
But Scott had some concerns, as well. He asked Regina, “How do these open findings impact our risk?”
Unfortunately, Regina couldn’t answer that. She was already so overwhelmed with the growing list of vulnerabilities and lack of standardized methodology that updating risk scores and reports was an afterthought. She needed help sifting through the chaos to prioritize remediation.
Contextualize Risk in Optics
Conner invited Regina to check out ZenGRC. The first thing that struck Regina was the ability to create Optics. Panda Partners has three applications — HealthApp, GovApp and GlobalApp — each with unique threats, vulnerabilities and controls. They also operate in two primary markets: Europe, the Middle East and Africa (EMEA) and North America. Regina created Optics for each!
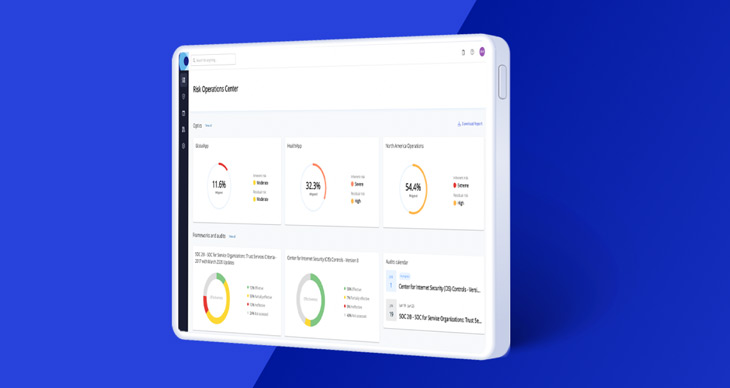
Automated Relationships
Within the Optic, Regina was enthralled by the automated connections between controls, vulnerabilities, threats and risks — and the importance of each within the risk calculation method.
She utilized the out-of-the-box threat and risk registers within ZenGRC to set a baseline inherent risk score within each Optic. She then worked with Conner to identify the various frameworks applicable to each Optic. As they began to align the Optics with Frameworks, Regina immediately saw the residual risk reduce. She was floored!
Risk Red Flag
Most organizations maintain a risk register; however, a clear definition of risk is often missing. “Risk” is used as an umbrella term to capture anything adverse that impacts the business. And when everything is a risk, nothing is a risk. Remember, if the event occurred, it’s not a risk. It’s a vulnerability or weakness that needs remediating.
ZenGRC connects risks to relevant threats, vulnerabilities and control implementations. As threats change or vulnerabilities are added, the relevant risks automatically increase.  And as evidence is collected and control implementations are marked as effective, risk automatically reduces. With ZenGRC able to produce an always-on risk score, Regina was free to focus on more valuable activities.
And as evidence is collected and control implementations are marked as effective, risk automatically reduces. With ZenGRC able to produce an always-on risk score, Regina was free to focus on more valuable activities.
Unified View of Risk
Gary, Conner and Regina now have a unified view of governance, risk and compliance framed around Panda Partners’ strategic business objectives.
ZenGRC enables them to automate many tedious tasks while building a solid foundation to scale in the future. The various dashboards, tables and formatted reports offer Scott the data-driven insights he needs to convert that risk into a business advantage.
See ZenGRC in action! Schedule your free demo today.




