
As global data privacy and cybersecurity regulations continue to increase, the pressure for organizations to manage compliance risk grows. The first step in your journey to better compliance risk management is compliance risk assessment.
With risk management methodologies, a compliance risk assessment analyzes how an organization might not meet its regulatory compliance obligations. This assessment should be a holistic analysis to identify all the compliance requirements that various laws, rules, and industry standards might impose on your organization. It evaluates whether or not your existing compliance program meets those expectations.
In this article, we will explain what a compliance risk assessment is, how to undertake one using established risk management methodologies, and how to implement your risk assessment’s findings after completion.
What Is Inherent Risk?
To begin, an organization should determine the amount of inherent risk it faces. Inherent risk is the potential harm when a risk is left untreated or ignored. Use a disciplined, objective method to analyze each risk’s likelihood and possible effect to help you understand the inherent risk you face. This also implies that the less a company tries to manage risk, the more risk it inherently has.
Understanding inherent risk allows a company to develop an early sense of the risk mitigation that might be necessary. When identifying inherent risk, companies should analyze the critical risk characteristics, which are divided into four categories:
Legal Impact
Legal or regulatory proceedings against the company or its workers may result in fines, penalties, incarceration, product confiscation, or debarment. Any time a company or its employees violate the law or compliance requirements, they are subject to legal issues.
Financial Impact
Financial impacts are the harm caused to the organization’s income statement, share price, or possible future earnings. Various compliance issues can generate an economic impact, including fines from legal matters, lost sales from reputational damage, or reduced cash flow from factory downtime.
Business Impact
Internal or external factors can impact a company’s day-to-day business operations. A failed new product can slow business growth, and political sanctions can disrupt the supply chain.
Reputational Impact
Negative media coverage (in traditional news or social media) damages the organization’s reputation or brand. Bad press can result in loss of customer trust and lower employee morale.
Measure each impact in qualitative and quantitative terms for a comprehensive view of risk. Qualitative research often uses a low-medium-high scale to express the magnitude of a risk. Since it is a more subjective measurement, creating definitions for each level of magnitude is crucial.
Quantitative assessments are numerical estimates of potential harm. For example, if you know your factory ships $1 million daily, you can calculate the impact for each day of downtime. Precision is preferred, but estimates are better than nothing.
What Is a Compliance Risk Assessment?
A compliance risk assessment analyzes how an organization might not meet its regulatory compliance obligations. This analysis should be holistic to identify all the compliance requirements that various laws, rules, and industry standards might impose on your organization and how well your existing compliance program does or doesn’t meet those expectations.
Common Compliance Risks
Innovative business leadership not only recognizes these risks but also effectively addresses them. Below are four prominent compliance risks that modern enterprises face all the time:
1. Data privacy infringement
The European Union’s General Data Protection Regulation (GDPR) revolutionized data privacy rules forever, giving consumers more control over their data. This regulation mandates data portability, breach notifications, child data protection, and more designed to empower consumers. Non-compliance leads to hefty fines, making strict adherence necessary.
2. Protected Health Information (PHI) mishandling
Complying with the Health Insurance Portability and Accountability Act (HIPAA) is crucial for organizations handling medical data. Neglecting proper risk assessment and procedures can expose sensitive patient data. Compliance measures include securing electronic patient records and implementing rigorous protocols to prevent data mishandling.
3. Lack of disaster preparedness
Natural or human-induced disasters pose significant threats to IT systems. Business continuity maintains daily operations during crises, while disaster recovery restores IT systems efficiently. Compliance with standards such as ISO 27031, SOC 2, NIST, and HIPAA demands a robust disaster recovery plan focusing on vulnerability identification, minimized disruption, team coordination, and regular drills.
4. Breach of payment card data
Backed by major card brands, the Payment Card Industry Data Security Standard (PCI DSS) guards against hackers targeting payment card data. Qualified Security Assessors (QSAs) certified by the PCI Security Standards Council play a pivotal role in safeguarding customer data.
What Does Compliance Risk Involve?
Compliance risk is the organization’s exposure to the potential consequences of non-compliance. What fines, penalties, or other costs might regulators impose if the business doesn’t meet its compliance obligations?
Monetary fines can be hefty. Other possible penalties include loss of operating licenses or disbarment from government contracts. Corrective actions can be expensive to implement. There would also be legal costs as regulators investigate, plus the potential for civil lawsuits and reputational loss among your customers.
Many regulators will offer more favorable treatment to a company that demonstrates a compliance program and is at least trying to meet its obligations.
A compliance risk assessment measures the gap between what your compliance program does versus what your compliance program should do to pass muster as an “effective” program in the eyes of regulators. Mitigation is the step to reduce your compliance risk until it achieves that effectiveness goal.
Before an organization can mitigate its compliance risk, however, it must conduct a compliance risk assessment.
Compliance Risk Assessment Steps
A comprehensive risk assessment will include several steps:
- Identifying risks
- Analyzing the level of the risk
- Determining what actions might be necessary to decrease the risk
- Implementing initiatives
- Evaluating the effectiveness
Here are each of the steps in more detail.
Step 1: Identifying Risks
Identify which regulatory compliance standards apply to your business, then document key workflows, information systems, and transactions. These efforts will require input from stakeholders of every business unit. Take note of areas in essential functions and procedures that suggest non-compliance with regulatory requirements.
Here’s how to identify compliance risks:
- Research regulations. Understand the laws and standards applicable to your industry.
- Internal audits. Evaluate your practices against compliance requirements through internal audits.
- Employee input. Encourage employees to report practices that could raise compliance concerns.
- Third-party evaluation. Assess compliance of vendors and partners.
- Analyze history. Study past incidents for patterns and recurring issues.
- Tech and data check. Review IT systems and data management gaps in compliance.
- Training review. Gauge the effectiveness of compliance training programs.
- Stay updated. Monitor evolving compliance regulations and industry trends.
- Benchmarking. Compare your practices with industry peers for insights.
- Consult experts. Seek guidance from legal or compliance professionals.
Step 2: Map Potential Risks to Possible Outcomes and Affected Parties
Once you’ve evaluated the company’s operations and where compliance gaps or risks may be, map those risks to their potential outcomes and affected parties. Not only is this critical documentation to have for auditing purposes, but it’s also a way to begin your risk mitigation strategies.
Step 3: Prioritize the Most Severe Risks and Determine Control Measures
Implementing new compliance programs (or improving existing ones) can be overwhelming. We recommend prioritizing all the identified risks by the potential severity of their outcomes and addressing the most severe first.
Ask: Where are existing controls failing to address those risks? How can you remedy that? Also, consider how you can detect a violation of the rules for these severe risks in the future. This consideration will reduce any non-compliance surprises.
Step 4: Implement Controls and Validate through Testing.
Once you’ve determined what must be done to mitigate compliance risks, implement those steps — but you’re not done there! Testing to validate controls is essential before proceeding to another risk. Review the results and decide whether the control works as desired. If not, investigate why, and if necessary, implement more or better controls to get the expected performance.
Step 5: Routinely Re-Evaluate Risks, Test Controls, and Update as Needed
Remember that a corporate compliance program should be an ongoing part of business. As the business grows, risks will change. Legislation affecting the business also evolves. Moreover, unmonitored, unenforced controls tend to lapse after a while. So, you should routinely monitor controls, re-test them periodically, and re-evaluate them as the business grows and laws change.
Compliance Risk Assessment Frameworks
The Committee of Sponsoring Organizations (COSO) framework for internal control is the most widely accepted framework for building internal control systems. For senior management and boards of directors, the COSO framework provides:
- Guidance to create and apply internal controls for any business, regardless of industry, at every company level.
- A principled approach for the organization to drive the design, implementation, and execution of its internal controls.
- Requirements to help ensure internal controls, components, and principles function and operate together.
- A way to identify and evaluate risks and develop the appropriate mitigation strategies is to maintain an acceptable level of risk with a focus on fraud prevention.
- Expanded control application beyond financial reporting to operational and compliance objectives.
- The ability to eliminate inefficiencies and redundancies in controls while maximizing value in risk reduction.
How Does Compliance Risk Assessment Differ From Other Risk Assessments?
Risk assessments exist for various business risks and industries, including financial services, government contracts, and healthcare.
Compliance risk assessments identify, prioritize, and control risks associated with the threat of non-compliance in your industry. Potential penalties could be fines, reputation damage, legal repercussions, or the inability to operate the business.
Unlike other forms of risk assessments, compliance risk assessments focus on the legal or regulatory requirements that an organization must comply with. Furthermore, risk analysis and compliance testing are typically managed by your compliance department’s chief compliance officer, who typically manages risk analysis and compliance testing.
The chief financial officer, the chief information officer, or another C-level executive might manage other risks.
How Internal Audits Aid in Compliance Risk Management
Internal audits are a critical part of the compliance risk assessment process. They help identify areas of high-risk exposure and gaps in compliance programs. Effective internal audits evaluate compliance with legal requirements and adherence to the organization’s risk management processes.
Internal auditors can provide an independent, objective assessment of the company’s compliance risk level. Their findings lead to action plans and remediation to improve compliance risk management.
Key elements of leveraging internal audits include:
- Developing an audit plan that covers high-risk areas and new regulatory changes
- Using risk identification techniques like interviews, document reviews, and data analysis
- Reporting detailed findings on compliance gaps and risk levels
- Making recommendations for remediating issues and enhancing compliance programs
- Following up to validate remediation efforts and risk reduction
Regular internal audits enable ongoing monitoring of compliance risk. They also provide valuable input for the organization’s annual compliance risk assessment process.
What Are the Best Practices for Conducting a Compliance Risk Assessment?
A practical compliance risk assessment follows structured best practices and involves key stakeholders. Here are some best practices to consider:
- Review applicable laws and regulations to identify legal requirements
- Rate each risk according to potential impact and likelihood
- Prioritize the most significant risks for remediation
- Develop risk mitigation plans that assign accountability
- Establish KPIs and metrics to monitor compliance risk levels
- Document risk assessment findings and management responses
- Schedule periodic reviews and updates as risks change
The assessment process should align with the organization’s established risk management system. Provide adequate resources and training to internal audit teams supporting the process.
Use technology like GRC software to collect, analyze, and report compliance risk data. Automation tools can streamline the assessment process.
Organizations can conduct efficient, comprehensive compliance risk assessments following these best practices. They provide the foundation for making strategic decisions to strengthen regulatory compliance.
How RiskOptics Can Support Compliance Risk Assessment
Evaluating risks, implementing the appropriate controls, and gathering documentation at every step can be time-consuming and prone to error if you rely on manual processes and tools such as spreadsheets.
The ROAR Platform is a governance, risk management, and compliance software tool that simplifies compliance efforts by automating tedious, manual tasks. Its easy-to-use risk management templates provide an outline to evaluate risk properly, while our user-friendly dashboard metrics show you where you’re doing well and where your gaps are in real-time, so you always know where you stand.
ROAR also tracks compliance training and documentation requirements across laws and regulations such as the EU General Data Protection Regulation (GDPR), California Consumer Privacy Act (CCPA), Health Insurance Portability and Accountability Act (HIPAA), and more.
Schedule a demo today to learn how the ROAR Platform streamlines compliance risk management.
Cybersecurity is ever-changing and a critical consideration for business survival. One must always be prepared to keep their business secure and their customers satisfied. But how do you keep up with all the compliance framework changes, such as last October’s SOC 2 guidance updates?
This was my challenge as the GRC manager at a SaaS startup: an updated compliance framework version would be released, and I’d need to figure out how to incorporate the new requirements. Assessing them, identifying gaps, educating teams and implementing the necessary changes filled me with anxiety.
ISO27001 was especially perplexing. Everything I read didn’t quite make sense, and I just wished someone had written a simple guide to the new framework requirements.
If you feel the same way about the new SOC 2 guidance — here is your guide!
What Is SOC 2?
SOC stands for “Systems and Organizations Controls.” It is a framework designed to help software vendors and other companies demonstrate the security controls they use to protect customer data in the cloud.
The American Institute of Certified Public Accountants (AICPA) is the governing body of the SOC framework. They set the U.S. auditing standards used for SOC 2 examinations and periodically review them.
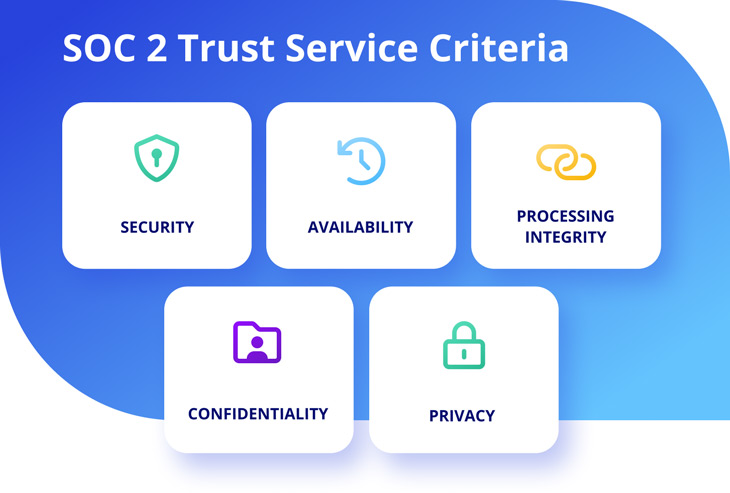
SOC 2 Trust Service Criteria
There are 5 Trust Service Criteria (TSCs) that make up the SOC 2 certification. Security is the only required TSC.
-
Security
Demonstrate systems are protected against unauthorized access and other information security risks that could impact the ability to provide the services promised to clients, including:
- Protection of Information: security of information during any activity including the collection or creation of the data, and during the use, processing, transmission and storage of the data.
- Protection of Systems: security of any systems that use electronic information to process, store or transmit information relevant to the services provided by the service organization.
-
Availability
Demonstrate systems are operationally available at all times so as not to impact a client’s business.
-
Processing Integrity
Demonstrate that system data processing and transactions occur accurately and in a timely manner on behalf of clients.
-
Confidentiality
The data custodian must demonstrate protection for data classified as confidential and/or identified and signed under a confidentiality agreement or an NDA (non-disclosure agreement), such as legal documents, bank statements, trademarks, etc.
-
Privacy
Demonstrate that personally identifiable information (PII) is protected and handled appropriately; for example, show that personal information is collected, used, retained, disclosed and destroyed in conformity with commitments in the organization’s privacy notice.
The description of the organization’s system is the largest and most critical section of the SOC 2 report. It includes the company’s overview: people, processes and technology that support the organization’s product, software or service. It also covers a description of all the controls that have been implemented with respect to the TSCs. This important information helps your auditor assess whether the system components are effectively protecting customer data.
What’s New with SOC 2?
The AICPA made significant guidance updates to the Description Criteria implementation and points of focus on the SOC 2 TSCs. These updates provide more examples.
The AICPA incorporated:
- New attestation standards
- Information about the risk assessment process and specific risks
- Additional clarity regarding certain disclosure requirements, such as how controls meet the requirements of a process or control framework
Revised SOC 2 TSC Points of Focus
The revised SOC 2 TSC points of focus provide guidance and clarity on:
- Incorporating new changes to CPA attestation standards
- Key differences between the Confidentiality and Privacy TSCs and when it’s appropriate to report on controls included in them
- Business objectives and how they relate to the service commitments and system requirements
- Identifying sub-service organizations versus vendors, appropriate types of controls or related disclosures and management’s use of specialists
- Identifying the use of software applications and tools that help with the detection of threats and vulnerabilities, such as firewalls, intrusion prevention and/or detection systems, etc.
- Improved controls supporting the implementation of the TSCs
- Addressing the landscape of changing technologies, threats, vulnerabilities and risks
- Addressing data management, including data storage, backup and retention as it relates to confidentiality
- Differentiating points of focus related to privacy as a “data controller” versus a “data processor”
- Considering the operation of periodic controls that operated prior to the period covered by the examination
Key SOC 2 Areas Impacted
The revised SOC 2 TSC points of focus impact the following criteria, identifying areas of improvement to strengthen operations:
-
Control Environment
The revised points offer clarity on the types of information relevant to systems of internal control:
- Information about data flow
- Asset inventory and location
- Information classification
- C&A (completeness and accuracy) of information used in the system
CC1.3 and CC1.5: addressing newly identified privacy concerns regarding reporting lines and disciplinary actions.
-
Information and Communication with Availability and Privacy
The revised points provide guidance on management’s identification of threats to data recoverability and mitigation procedures to better align with widely used privacy practices.
CC2.1: addressing the management, classification, C&A and storage of assets.
CC2.2: addressing communication concerns relating to privacy knowledge and awareness and reporting of incidents related to privacy (*when Privacy TSC is applicable).
CC2.3: addressing communication of incidents related to privacy (*when Privacy TSC is applicable). -
Risk Assessment
The revised SOC 2 TSC points help with identifying a more granular approach to evaluating risks by understanding the underlying components of a risk assessment:
- Threat and vulnerability identification
- The evaluation of the likelihood and magnitude of a threat event intersecting with a vulnerability
CC3.2: addressing the identification of system component vulnerabilities and providing additional guidance on assessing the significance of risks for the sub-service organization.
CC3.4: assessing changes in internal and external threats and vulnerabilities the organization may encounter. -
Logical and Physical Access
The updated TSC points encourage consideration of logical access controls across the system architecture, including all relevant:
- Infrastructure
- IT tools
- Types of access, such as employee, contractor, vendor or business partner
- System and service accounts
- Recovery of devices, such as laptops
CC6.1: addressing the access and use of confidential information for identified purposes (*when Confidential TSC is applicable).
CC6.4: addressing the recovery of physical devices. -
System Operations and Monitoring
The revised SOC 2 TSC points encourage the consideration of activities performed by the first and second lines of defense; for example, monitoring performed by those performing a task and by managers who oversee them, respectively.
This is in addition to internal audit functions and other recurring information technology (IT) assessments that have historically been identified in their SOC 2 reports.
CC7.3: addressing the impact on, use or disclosure of confidential information in the case of a security event occurring (*when Confidential TSC is applicable).
CC7.4: addressing the definition of and execution of breach response procedures (*when Privacy TSC is applicable). -
Change Management
Identification, testing and implementation of software patches and resilience requirements during the change management process are also covered in the revised SOC 2 TSC points.
CC8.1: addressing the process for managing patch changes and the design and testing phases for system resilience (*when Availability TSC is applicable) and privacy requirements in the design phase (*when Privacy TSC is applicable).
-
Risk Mitigation
The updated TSC points offer direction on residual risk after considering internal controls and management’s decisions to accept, reduce or share risks.
CC9.2: addressing the identification and evaluation of vulnerabilities arising from vendor and business partner relationships.
How Do the SOC 2 Updates Impact Companies?
This new SOC 2 guidance is intended to help organizations better meet the information needs of their customers and business partners when considering technological threats and vulnerabilities, as well as confidentiality and privacy issues.
No new TSCs were added or even changed
Nor does every point of updated guidance in the design implementation and operations of controls need to be met, as they are not strict “requirements.”
However, these revisions are effective immediately and will enhance the usefulness of SOC 2 reports for evaluating an organization’s security posture.
Auditors use SOC 2 guidelines to attest to a company’s compliance and security practices. The majority of the updates focus on the privacy and confidentiality TSCs to help clarify the application of existing criteria to new technologies and evolving risks in light of the current landscape. SOC 2 assessors performing examinations will take these into consideration.
Organizations should consider these revisions and incorporate relevant changes to improve clarity and processes, as well as to best represent their service commitments.
What Are the Benefits of SOC 2?
Are you wondering what the benefits of SOC 2 are and why an organization should comply?
Getting SOC 2 improves your information security credibility. It demonstrates that you’re
protecting customer data, which can establish trust, drive revenue and unlock new business opportunities.
Key benefits of SOC 2:
-
Customer Demand
Protect your customer data from unauthorized access and theft.
-
Cost Effectiveness
Avoid costly security breaches and the financial and collateral reputation damage that comes with them.
-
Competitive Advantage
Gain an edge over competitors that can’t show compliance.
-
Peace of Mind
Develop strong policies and procedures, assure customers your systems and networks are secure and provide valuable insights into your risk and security posture.
-
Regulatory Compliance
Attaining SOC 2 can accelerate your organization’s overall compliance efforts for other frameworks, such as ISO and HIPAA. Plus, it’s an alternative to time-consuming, 500-question security questionnaires!
SOC compliance isn’t required by law, but it is considered the gold standard for companies to prove their commitment to customers. It demonstrates they protect customer’s data and make their services reliable, resilient and consistent. In fact, many enterprises won’t do business with technology vendors or other service providers that haven’t achieved the SOC 2 attestation.
All SOC 2 audits must be completed by an external auditor from an accredited and licensed CPA firm. If not, there is no credibility of the certification. When performed correctly, the SOC 2 certification gives a professional opinion that the processes declared are actually being followed in practice. This valuable information can be shared with clients and prospects alike.
Get SOC 2 Ready with ZenGRC
Whether you’re seeking SOC 2 certification for the first time or need to stay ahead of recent regulatory changes — the ZenGRC can help simplify the process.
ZenGRC gives you the ability to see, understand and take action on your IT and cyber risks. With a unified, real-time view of risk and compliance — framed around your business priorities — you’ll have the contextual insight needed to easily and clearly communicate with key stakeholders. That way, leadership can make smart, strategic decisions to protect your enterprise, systems and data. And your organization can earn the trust of your customers, partners and employees.
Discover the power of the ZenGRC Platform! Schedule your FREE demo today.



