For merchants who process payment cards, compliance with the Payment Card Industry Data Security Standard (PCI DSS) is mandatory for doing business. While PCI DSS establishes prescriptive requirements for protecting data, many companies struggle with understanding how to determine what networks and systems fall within the PCI DSS scope. For many merchants, the most frustrating and confusing part of maintaining compliance with the PCI Security Standards is determining what networks and system components need to be protected under the rigorous standard.
Understanding PCI DSS
What is the Payment Card Industry Data Security Standard?
The five major payment card companies, American Express, Discover Financial Services, JCB International, MasterCard, and Visa, Inc. banded together to create the Payment Card Industry Security Standards Council (PCI SSC) to establish best practices for protecting cardholder data. The organization wanted to create a series of standards for how to process payments – to protect their customers as well as themselves. These became the Payment Card Data Security Standard.
What is cardholder data (CHD)?
The standard defines CHD as any personally identifiable information (PII) that can link an individual to their a credit or debit card. This card data includes the primary account number (PAN) in combination with either the cardholder name, expiration date, or service code.
What is the cardholder data environment (CDE)?
Under the standard, any computer or networked system that processes, stores, or transmits this CHD needs to be protected using the specified controls listed in the PCI DSS requirements. The CDH includes system components such as network devices, servers, computing devices, and applications. These can be security services, virtual components, network components, server types, applications, or anything connected to CDE.
The standard defines “system components” as network devices, servers, computing devices, and all applications, providing six specific examples:
- Security services, segmentation services, or services impacting security
- Virtual components including machines, switches/routers/appliances, applications/desktops, and hypervisors
- Network components
- Server types
- Internal and external applications
- Anything connected to CDE
What is network segmentation?
Under the PCI standard, your CDE needs to be separated from any other systems, software, and networks used within your enterprise. Any unprotected connection to the CDE, internal or external, places your organization at risk for fines.
What is PCI DSS scope?
PCI compliance starts with determining your CDE. Determine what systems, networks, devices, and applications store CHD, and therefore are part of your CDE, is the process of deciding your PCI scope. All these systems, devices, networks, and applications that need to be separated from the rest of your IT infrastructure and protected by the prescriptive requirements.
Why do I need to create a data flow?
Understanding your IT infrastructure not only requires you to focus on the individual system components that store, process, and transmit data, but also the way the data moves between them. For example, if CHD travels across a network and that network also transmits data for an application that does not impact CHD, the app is also connected to your CDE.
Therefore, you need to apply the PCI controls to that application as well to ensure the security of the CDE. If you don’t protect that application, a malicious actor can use it to obtain unauthorized access to your network which ultimately puts cardholder data at risk. Understanding the way data flows not only within your CDE but across your entire infrastructure allows you to ensure stonger threat mitigation.
What is an SAQ?
To ease the burden on merchants using vendors to enable PCI compliance, the PCI Security Standards Council created a Self-Assessment Questionnaire that allows you to review your technologies to see if they meet the data security requirements. For businesses that use PCI SSC approved point-to-point encryption (P2PE) hardware, this streamlines the requirements by more clearly defining, and limiting, the CDE.
A P2PE is a device used in brick-and-mortar (card present) and mail/telephone order merchants. To qualify for this lower standard, the merchant must attest that they
- only process payments using a P2PE device approved by the PCI SSC
- the only devices that interact with P2PE device are supported Point of Interaction (POI) devices approved for use with it
- have no other electronic storage, transmission, or collection locations for cardholder data
- do not store legacy information electronically
- have implemented all the controls required by the P2PE solution.
In this case, the merchants limit their PCI scope to just these devices and their technologies.
What is a Qualified Security Assessor (QSA)?
Your QSA is the external party certified by PCI SSC who oversees your PCI compliance. In short, they act as external auditors who go through PCI specific training.
As such, the first thing they will look at when they review your PCI compliance is whether you have appropriately scoped your CDE. If you haven’t correctly defined your compliance scope, then you won’t be able to set related controls in compliance with the requirements. Thus, before they review any other controls, they will determine whether you’ve located all the right system components.
What about service providers?
As merchants increasingly use Software-as-a-Service (SaaS) platforms to make payment processing easier, those suppliers are also in-scope systems for PCI compliance if they transmit, store, or process CHD.
Your service level agreement (SLA) should clearly outline the PCI-DSS requirements covered by you and the services provider.
To prove its compliance, your vendor needs to provide documentation assuring:
- Annual assessment done independently and provided to their users.
- Multiple on-demand assessments at the request of each client.
If the service provider chooses to do its own annual assessment, the customers need to make sure that it covers their compliance needs and is part of the contract.
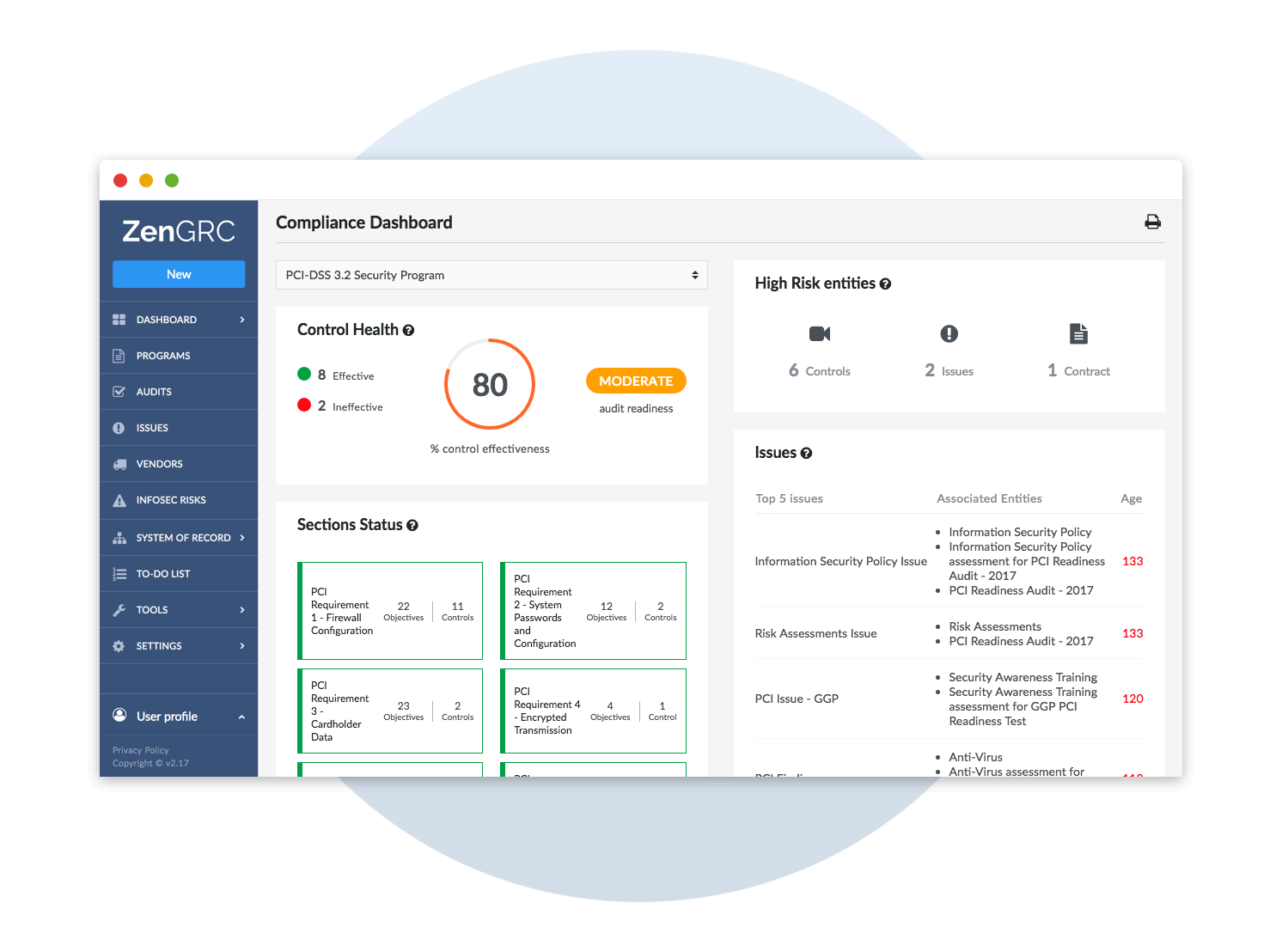
How to Use ZenGRC for PCI Compliance
ZenGRC acts as a single source of information for PCI compliance. With ZenGRC’s built in PCI mapping capabilities, you can easily align your current controls to the standard’s requirements.
Moreover, ZenGRC’s dashboard provides real-time insights into your organization’s control effectiveness providing you with continuous monitoring capabilities as required by PCI.
The workflow management and risk management capabilities within the ZenGRC platform offer merchants a way to communicate with internal stakeholders to ensure that you manage high priority risks first.
For more information about how to determine your PCI scope and protect your CDE, download our ebook “PCI DSS: Steps to Successful Scoping.”



