
Intro
The Payment Card Industry Data Security Standard (PCI DSS) is an information security framework intended to help merchants and service providers protect credit and debit card transactions from data breaches.
PCI DSS is not a law or regulation but an industry mandate. If your enterprise accepts credit card payments or handles payment card data, it must comply with PCI DSS.
PCI DSS’s origins date to 1999, when Visa developed a Cardholder Information Security Program in response to rampant increases in credit card fraud via the (new) Internet. Other major credit-card brands—Mastercard, Discover, American Express, and JCB—followed suit with their own security programs. In 2004 these five jointly launched PCI DSS 1.0.
In 2006, the card brands added financial institutions, merchants, processor companies, software developers, point-of-sale (POS) vendors, and others to their security initiative, forming the PCI Security Standards Council (PCI SSC). The council made the first revisions to the standard, PCI DSS 1.1.
Subsequent revisions have been issued since. All merchants as well as payment and internet service providers that process, store, or transmit transactions involving any of these cards must comply with PCI DSS.
How can you know if you’re doing PCI DSS right? Relax—we’re here to help. This guide is chock-full of information about all aspects of this important security framework. If you want a deeper dive, you’ll find links to our many posts about PCI DSS topics as well as an eBook to help you prepare for your PCI audit or self-assessment.
Vigilance is Key. PCI DSS compliance is not easy. Its 281 directives in 12 categories can take years to fulfill. And obtaining an auditor’s Report on Compliance (ROC) or filing an Attestation of Compliance (AOC) with your organization’s acquiring bank is just the beginning.
The PCI SSC demands that entities not only become PCI DSS compliant but also demonstrate a continual commitment to securing credit card data.
To maintain these rigorous standards, you must be ever-vigilant. Because the price of non-compliance with PCI DSS can be high—even crippling to your business.
What is PCI Compliance?
Compliance with the Payment Card Industry Data Security Standard (PCI DSS) means adhering to the 12 requirements established by the PCI Security Standards Council.
The PCI DSS requirements are:
- Install and maintain a firewall configuration to protect cardholder data.
- Do not use vendor-supplied defaults for system passwords and other security parameters.
- Protect stored cardholder data.
- Encrypt transmission of cardholder data across open, public networks.
- Use and regularly update antivirus software.
- Develop and maintain secure systems and applications.
- Restrict access to cardholder data by business need-to-know.
- Assign a unique ID to each person with computer access.
- Restrict physical access to cardholder data.
- Track and monitor all access to network resources and cardholder data.
- Regularly test security systems and processes.
- Maintain a policy that addresses information security.
Within each requirement are a number of directives—281 in all—for achieving compliance with the framework. Every merchant that accepts one or more of the major card issuers—Visa, Mastercard, American Express, Discover, or JCB—via e-commerce or in-store must be PCI compliant. The process can take up to two years for larger merchants, and one year or more for mid-sized and smaller ones.
In addition, every service provider that processes, stores, or transmits credit card data, or those for whom a breach might threaten to compromise card or cardholder data, must comply with this important security framework.
How To Demonstrate PCI Compliance
To demonstrate PCI compliance, larger entities (Level 1) will need an on-site audit by a Qualified Security Assessor (QSA) or an Internal Security Assessor. If you pass the audit, the assessor will file a Report on Compliance (ROC) with your acquiring bank.
Mid-size and smaller enterprises (Levels 2, 3, and 4) may be able to forgo the audit, and instead complete a self-assessment questionnaire (SAQ) and file an Attestation of Compliance (AOC).
PCI compliance happens not just once, but continually. Maintaining compliance includes staying abreast of changes, and modifying your security policy and controls as revisions occur.
One of the most important PCI requirements is that organizations completely disable Secure Socket Layer and early Transport Layer Security (TLS 1.0) encryption. These protocols are outdated, no longer meeting security standards for encryption of data transmitted over public networks. The PCI SSC now requires the use of TLS 1.1 or, preferably, TLS 1.2.
To Whom Does PCI DSS Apply?
PCI DSS applies to all merchants in the retail industry that accept credit card payments from customers using Visa, Mastercard, American Express, Discover, or JCB.
PCI compliance is also required of certain service providers, including those providing payment services or internet services, such as Amazon Web Services (AWS).
If a breach of your organization’s systems or network could compromise credit card customer data, you must comply with PCI DSS. And then, year after year, you must be continually PCI compliant, vigilant about securing the customer data of individuals as well as enterprise-scale customers. Hackers never let up, and neither can your organization.
PCI Compliance: How To Get Started
Many merchants and service providers embark on the journey to PCI DSS compliance by forming a committee. This committee is responsible for determining the scope (which PCI DSS compliance level and directives apply to the organization) as well as overseeing:
- Establishment and testing of controls related to payment processing security,
- Remediation of control gaps and security vulnerabilities,
- Gathering of evidence demonstrating compliance efforts and the results, and
- Maintenance of PCI DSS compliance over time.
Committee members should hail from a variety of areas in the organization, and represent various roles including executives.
Areas represented might include
- Information technology (IT)
- Information security
- Auditing
- Legal
- Risk management
- Compliance
- Finance
- Business affairs
- Human resources
Members’ roles might include
- PCI Compliance Manager/Project Manager
- Chief Information Security Officer
- Risk Manager/Officer
- Legal counsel
- System administrator
- Business analyst
- E-commerce platform developer
Why is PCI DSS Compliance Important?
- It protects consumers’ personal information from unauthorized access and use
- It protects financial accounts from theft
- It protects businesses from the harsh penalties non-compliance can bring
Why PCI DSS Was Created?
When e-commerce debuted in the 1990s, so did its evil twin, cybercrime. Making a credit card purchase online was fraught with peril, as hackers stole not only access to users’ accounts but also their personal information.
Soon, in-store purchases posed similar threats: the remote connections over which merchants processed credit card payments got hacked, as well.
In response to concerns over the security and privacy of credit card and cardholder data, a coalition of credit card brands—Visa, Mastercard, American Express, Discover, and JCB jointly released PCI DSS 1.0 in 2004, and in 2006 formed the Payment Card Industry Security Standards Council (PCI SSC).
Comprising financial institutions, merchants, processor companies, software developers, and point-of-sale vendors, the PCI SSC in 2006 launched the first revision of the Payment Card Industry Data Security Standard, PCI DSS 1.1.
Who needs PCI compliance?
PCI DSS compliance is mandatory for all merchants and service providers that accept, process, transmit, or store payment card information.
Who enforces PCI compliance?
PCI DSS compliance is mandatory for all merchants and service providers that accept, process, transmit, or store payment card information.
The PCI Security Standards Council (PCI SSC) administers the framework, but the major credit card companies that formed the council (Visa, Mastercard, American Express, Discover, and JCB) enforce it.
Who governs PCI compliance?
While the PCI Security Standards Council is responsible for managing the PCI DSS and its standards, each payment card brand has defined its own requirements for compliance validation and reporting, such as provisions for performing self-assessments, and when to engage a Qualified Security Assessor (QSA) to perform an on-site compliance audit.
Who regulates PCI compliance?
The five major credit card brands on the PCI SSC regulate compliance with PCI DSS. Since acquiring banks have to be PCI compliant, too, however, they often insist that the merchants for whom they process payments comply with the framework. Self-assessment questionnaires (SAQ), Attestation of Compliance, vulnerability scan reports, and Reports on Compliance (ROC) are all submitted to acquiring banks.
Why PCI DSS Compliance Matters
A chain is only as strong as its weakest link. Fighting cybercrime is the impetus behind PCI DSS, which is why the PCI SSC designated harsh penalties for those who do not comply with the framework.
Those penalties may include hefty fines of $5,000 to $100,000 per month until an organization becomes PCI compliant, and possible loss of credit-card-processing privileges, which could cripple and possibly devastate a business.
Penalties aside, suffering a breach can be so costly—$148 per compromised record on average, according to a 2018 study—and can also take a major toll on a business’s reputation. So instead of asking, “Why PCI DSS?” a better question is, “Why not?”
PCI Compliance Requirements and Levels
The amount of risk an organization faces depends on a variety of factors. Recognizing these differences, the PCI Security Standards Council developed four PCI DSS compliance levels and validation requirements for merchants, and two for service providers.
The level your enterprise belongs to depends upon:
- How many credit card transactions you process in a year,
- Which credit cards you accept, and
- Whether your enterprise has suffered a breach or cyberattack resulting in compromise of credit card or cardholder data.
Level 1 merchants and service providers process the most transactions in a year—1 to 6 million and more, depending on the card. They must meet the most stringent requirements for validating compliance.
For instance, Level 1 merchants must pass a yearly, on-site audit by a Qualified Security Assessor (QSA) or Internal Security Assessor, while those on lower levels can forgo the audit and complete a self-assessment questionnaire, instead.
The different levels determine how your organization validates its PCI compliance, but not which of the PCI DSS requirements it must meet.
What are the 6 PCI DSS goals and 12 requirements?
-
Build and maintain a secure network.
- Install and maintain a firewall configuration to protect cardholder data.
- Do not use vendor-supplied defaults for system passwords and other cybersecurity parameters.
-
Protect cardholder data.
- Protect stored cardholder data.
- Encrypt transmission of cardholder data across open, public networks.
-
Maintain a vulnerability management program.
- Use and regularly update anti-virus software or programs
- Develop and maintain secure systems and applications.
-
Implement strong access control measures.
- Restrict access to cardholder data by business need-to-know.
- Assign a unique ID to each person with computer access.
- Restrict physical access to cardholder data.
-
Regularly monitor and test networks.
- Track and monitor all access to network resources and cardholder data.
- Regularly test security systems and processes.
-
Maintain an information security policy.
- Track and monitor all access to network resources and cardholder data.
- Maintain a policy that addresses information security for employees and contractors.
All merchants and service providers that process, store, or transmit credit card data must meet these goals and requirements. Nested within the 12 requirements are 281 directives. Which apply to your organization depends on your unique situation, and will differ from enterprise to enterprise.
PCI Compliance Checklist
The Payment Card Industry Data Security Standard (PCI DSS) sets stringent rules for the security and privacy of credit card transactions as well as card and cardholder data.
Becoming PCI compliant is time-consuming, taking up to two years to achieve. But the framework’s 12 requirements and 281 directives are highly prescriptive, spelling out in detail what merchants and service providers must do to comply.
To sail through your organization’s audit or self-assessment with ease, we recommend the following steps to compliance:
-
Determine your scope.
Scrutinize all the requirements and directives and determine which pertain to your enterprise. Doing this will take some time, but will pay off in the long run by saving you and your Qualified Security Assessor (QSA) or Internal Security Assessor work at audit time or as you’re completing your self-assessment questionnaire (SAQ).
Requirements address the security of your cardholder data environment (CDE) from end to end and cover access control, your information security policy and parameters, maintaining a secure network, your vulnerability management program, and more.
-
Minimize your scope.
Pre-audit or self-assessment, you can take concrete actions to minimize the risk to your payment card data and devices, including
- Limit access to your CDE with firewalls.
- Encrypt all payment card data, point-to-point.
- Analyze your third-party-vendor functions.
- Analyze your third-party connections.
- Segment your networks.
- Dispose of cardholder data promptly and effectively.
-
Determine how well you meet each applicable requirement.
Examine each item on your list of relevant directives and ask, “How well does my organization comply?”
-
Test all controls related to your CDE.
Even if you have done this before, you must test each control anew—your evidence must be current.
-
Gather your evidence.
Having documentation of your compliance efforts and results on hand will save your auditor time and work, and save your enterprise money.
And remember: reaching compliance with the PCI Data Security Standard is only the first step.
The PCI Security Standards Council (PCI SSC) mandates ongoing, continual efforts to safeguard financial information against unauthorized access and use. After all, cybercriminals never let up—and neither should any enterprise entrusted with their customers’ and clients’ sensitive, private data.
Where Do I find the PCI Data Security Standard (PCI DSS)?
The PCI Security Standards Council has posted the PCI DSS in PDF format in the document library on its website. A drop-down menu at the top of the page allows you to filter for PCI DSS Self-Assessment Questionnaires (SAQ).
The Payment Card Industry Data Security Standard: Requirements and Security Assessment Procedures provides an overview of the PCI DSS framework to help you understand just what is PCI compliance, plus a complete list of the current PCI DSS requirements, directives, and sub-directives.
The document also includes appendices listing acceptable compensating controls that you may use, as well as a flow chart to help with the segmentation of your cardholder data environment from the rest of your system.
PCI DSS 4.0: What Changes Can We Expect?
The PCI Security Standards Council has set four goals with Version PCI 4.0:
- Make sure the standard still meets the security requirements of the payments industry
- Add support and flexibility of additional security methodologies
- Encourage security to be a continual process
- Improve validation methods
How Much Does PCI Compliance Cost?
The costs associated with PCI DSS compliance vary and depend on such factors as business type, company size, the security culture at your enterprise, and the card processing methods used.
Enterprises that hire a Qualified Security Assessor (QSA) to perform an on-site audit and complete a Report on Compliance (ROC) could pay $50,000 or more for the audit and report and for quarterly vulnerability scans, penetration testing, employee security training, and policy development.
If you have dedicated PCI staff, those salaries will factor into the equation, as well. And if the auditor finds compliance gaps or vulnerabilities, expect to pay remediation costs.
An on-site audit is required only for Level 1 merchants and service providers, but many Level 2 and 3 entities choose to comply at this level.
Organizations submitting an Attestation of Compliance and self-assessment questionnaire can save on third-party-audit expenses but often must pay someone to complete the forms. Other costs include quarterly vulnerability scans of your network environment, security training, and remediation. Estimates range from $60 per month for small businesses to $50,000 for those with multiple IP addresses.
In addition, credit card processors may charge a PCI compliance fee of $70 to $120 per year. Although you may wonder how to avoid paying this fee, the expense may be worthwhile if your processor provides PCI DSS compliance support such as vulnerability scanning and assistance with the self-assessment questionnaire.
How To Comply with PCI DSS: Steps to Take
The steps you must take to become PCI compliant begin with thoroughly familiarizing yourself with the security framework:
- The three pillars of PCI DSS
- Focused on credit card data
- Protecting stored data
- Annual validation
- The six PCI DSS goals
- The 12 PCI DSS requirements
- The 281 OCI DSS directives and sub-requirements
- The four PCI DSS compliance levels
Once you’ve examined PCI DSS and determined your enterprise’s PCI level and scope, take these steps to reach compliance:
- Create a cardholder data flow chart to identify each component of your organization’s cardholder data environment (CDE). Your PCI compliance manager and IT staff may work together to create this chart.
- Minimize your scope.
- Segment your cardholder data environment (CDE), including point-of-sale devices, from the rest of your system.
- Encrypt all data going into and out of your CDE using Transport Layer Security (TLS) 1.1 or higher.
- Ensure that your third-party vendors are PCI compliant.
- Promptly dispose of all payment card data that you do not need to store.
- Evaluate your compliance with each applicable PCI DSS directive, and remediate where necessary.
- Test your controls and get a pre-audit risk assessment—even if you have done so before.
- Document everything, and present those documents to your auditor or assessor.
- Create an ongoing PCI DSS monitoring program. Compliance with PCI DSS is not a one-and-done task but must be continually maintained.
These steps are important to follow whether you anticipate an on-site audit resulting in a Report on Compliance or plan to submit a self-assessment questionnaire (SAQ) and Attestation of Compliance (AOC) to your acquiring bank.
Using a third-party payment processor can make compliance easier. For instance, Amazon Web Services already files an AOC that your auditor or assessor can use to demonstrate compliance for that portion of your cardholder data environment.
What is a PCI Compliance Audit?
A Payment Card Industry Data Security Standard (PCI DSS) compliance audit examines the security of your organization’s entire credit card processing system, including:
- Point-of-sale system
- Mobile devices, personal computers, and servers
- Wireless hotspots
- Internet shopping applications
- Paper-based storage systems
- Cardholder data transmission
- Remote-access connections, especially over public networks
During this process, a Qualified Security Assessor (QSA) or your own Internal Security Assessor will determine the effectiveness of the information security controls around your Cardholder Data Environment (CDE).
To achieve a passing Report on Compliance (ROC), your organization must meet as many as 281 directives detailed in the 12 PCI DSS requirements.
The audit or assessment involves testing your
- Point-of-sale system
- Access (including physical access) to the CDE
- Third-party vendors’ data security
- Service providers’ PCI DSS compliance
- Network segmentation
- Payment-processing application
- Card-information storage location and process
- Router data security
- Data encryption
The auditor will also want to examine your documentation. Your PCI compliance document checklist should include these files:
- Risk assessment
- IT architecture
- Security policy
- Log monitoring reports
- Third-party agreements
- Audit trail files
- Information on security tools and applications (encryption tools, anti-virus software, etc.)
- Pre-audit assessment
This last item—pre-audit assessment—is critical to success. Even if you have already tested your CDE security controls, you must test them again before your audit to provide current evidence that they are working properly.
Do I Need a PCI DSS Compliance Audit?
Not every merchant and service provider must submit to an audit for PCI compliance.
Because different-sized businesses face different information security risks, the PCI Security Standards Council established four compliance levels for merchants and two for service providers. The levels differ slightly among the five major credit card brands (Visa, Mastercard, American Express, Discover, and JBS) but the requirements for each level apply across the board.
Those deemed to face the highest risk of data breach belong to Level 1 and must pass a yearly onsite audit. Level 1 includes:
- Merchants processing more than 1 million or more than 6 million total—e-commerce and in-store—credit card payments annually (the amount depends on which cards you accept)
- Service providers processing, storing or transmitting more than 300,000 credit card payments annually
- Any merchant or service provider that has experienced a data breach resulting in the compromise of credit card data
Those in levels 2, 3, and 4 may avoid an audit, instead of completing a self-assessment questionnaire and Attestation of Compliance (AOC). In some instances, however, acquiring banks may require an audit and ROC, especially for larger Level 2 merchants.
Other requirements for PCI compliance may include penetration testing and periodic vulnerability scans.
PCI Compliance vs. PCI Certification - What's the Difference?
The notion that any organization can be PCI-certified is a common misconception. Actually, there is no such thing as “PCI certification” or a PCI certification audit.
PCI DSS is all about protecting the privacy and security of credit card and cardholder data. Your organization’s audit or self-assessment will center on compliance with the 12 PCI DSS requirements and their 281 directives.
To achieve PCI DSS compliance, your enterprise must attain one of the following:

A Report on Compliance (ROC) after an on-site audit by a Qualified Security Assessor (QSA) or Internal Security Assessor
An Attestation of Compliance (AOC) filed by your organization with a self-assessment questionnaire
What is an SAQ for PCI Compliance?
The Payment Card Industry Data Security Standard (PCI DSS) Self-Assessment Questionnaires (SAQs) are tools provided by the PCI Security Standards Council (PCI SSC) to help credit-card-processing merchants and service providers measure their own compliance with the PCI DSS.
Organizations that do not need an on-site audit by a Qualified Security Assessor (QSA) or Internal Security Assessor with the resulting Report on Compliance (ROC) are permitted, instead, to self-assess. SAQs contains two components:
- Questions relating to the PCI DSS requirements
- An Attestation of Compliance (AOC), to be filed with your acquiring bank
To achieve PCI DSS compliance, your enterprise must attain one of the following:
The PCI SSC has developed eight merchant SAQs and one for service providers. The correct type for your organization depends on a number of factors, including how you process credit card transactions, the tools you use to do so, and whether you engage in e-commerce sales or in-store-only sales.
Here’s a summary of the PCI DSS SAQ types and their intended users:
- SAQ A: For merchants doing business remotely (e-commerce, mail order, telephone order) that have outsourced payment card data processing and storage to a PCI DSS-validated third party, and do not store card or cardholder data in any form
- SAQ A-EP: For e-commerce merchants that have outsourced credit card data processing and storage to a PCI DSS-validated third party but also maintain a website that doesn’t receive cardholder data but could affect the security of a payment transaction
- SAQ B: For merchants conducting sales in person using credit card imprint machines or standalone, dial-out terminals that do not store cardholder data electronically
- SAQ B-IP: For merchants conducting sales in person using only standalone, PIN Transaction Security (PTS)-approved card payment terminals with an internet protocol (IP) connection to the payment processor, and that do not store electronic cardholder data
- SAQ C-VT: For merchants who manually enter a single transaction at a time via a keyboard into an Internet-based, virtual payment terminal solution that is provided and hosted by a PCI DSS-validated third-party service provider. SAQ C-VT merchants may not store electronic cardholder data.
- SAQ C: For merchants conducting sales in-person using payment application systems connected to the Internet. SAQ-C merchants do not store electronic cardholder data.
- SAQ P2PE: For merchants using only hardware payment terminals included in and managed via a validated, PCI SSC-listed Point-to-Point Encryption (P2PE) solution, with no electronic cardholder data storage. Not applicable to e-commerce channels.
- SAQ D for Merchants: For all merchants not included in descriptions for the above SAQ types
- SAQ D for Service Providers: For all service providers defined by a payment brand as eligible to complete an SAQ
How To Scope PCI DSS For an Audit
To comply with PCI DSS can take a lot of time, effort, and expense—as long as two years and tens of thousands of dollars just to get there the first time. But you can greatly reduce the scope of your organization’s PCI audit or Self-Assessment Questionnaire (SAQ) by following a few simple guidelines, including:
Diagram the flow of cardholder data through your network.
A good CDE network diagram will show your network’s:
- Computing and networking devices
- Servers
- Switches
- Routers
- Applications
Segment your CDE from the rest of your network.
PCI compliance starts with network segmentation: installing firewalls between your CDE and corporate network and between your CDE and public network. Doing so will limit your audit or self-assessment to the CDE only.
Encrypt or mask cardholder data.
Tokenization of primary account numbers (PAN) means that the merchant never sees those numbers.
Store card data only for as long as you need it.
Dispose of cardholder data as soon as you can, and avoid PAN storage, if possible.
 The Reciprocity guide, “Preparing for a PCI DSS Audit: Five Steps to Success,” provides helpful tips and tricks for identifying and minimizing your organization’s PCI DSS audit or self-assessment scope, and reaching PCI compliance with relative ease. Download your copy now, and be ready at audit time.
The Reciprocity guide, “Preparing for a PCI DSS Audit: Five Steps to Success,” provides helpful tips and tricks for identifying and minimizing your organization’s PCI DSS audit or self-assessment scope, and reaching PCI compliance with relative ease. Download your copy now, and be ready at audit time.
What Happens If We Fail PCI Compliance?
The consequences for ignoring or failing PCI DSS compliance are dire. Fines of up to $100,000 per month for PCI non-compliance are only the beginning. When banks get the notification that you have failed to comply, it’s usually because your CDE has been breached.
Here are some of the expenses you could incur should your organization’s card and cardholder information become compromised:
- Costs of a PCI DSS forensic investigation
- Lawsuits
- Remediation costs (to fix the problem so it doesn’t happen again)
- Increased rates charged by banks and/or processors
- Federal Trade Commission audits
- Notification costs
- Costs of compensation to affected customers, which may include
- Credit monitoring
- Identity theft insurance
- Card re-issuance
- Cancellation of your credit card acceptance privileges
Also, a breach that compromises credit card data moves your enterprise, no matter how small, to PCI Compliance Level 1. This most stringent PCI DSS compliance level requires expensive on-site audits every year, network vulnerability scans every 90 days, and, for service providers, penetration tests and internal scans.
In the case of a failed PCI DSS compliance scan of your networks, it’s critical to remediate immediately. PCI DSS is considered the baseline for data security—the minimum security measures your organization needs—and any system vulnerabilities are ripe for exploitation.
With 12 requirements and 281 directives, however, the PCI checklist for audits can feel intimidating even to large businesses.
For instance, does your organization store credit card personal account numbers (PAN)? PCI DSS requires that the PANs be stored in an “unreadable” format, with hashes, tokens, truncation, or strong cryptography (although it discourages storing these numbers at all). If you are not protecting this sensitive information now, you must do so.
Ignore the PCI DSS requirements at your own peril. Compliance is mandatory—with no exceptions—for every entity that processes, stores, or transmits credit card information. The costs can be high, but non-compliance could literally break your bank account.
Surprisingly, many businesses fail to meet the standard: A 2018 survey of retailers, for instance, found that 91 percent did not comply with PCI DSS.
Fortunately, you can get PCI compliance assistance from ZenGRC. Our user-friendly compliance software has checklists, “single source of truth” dashboards, easy internal scans and audits, and more to ensure that your organization stays secure and in perpetual PCI DSS compliance.
Best Ways to Maintain PCI Compliance
Payment Card Industry Data Security Standard (PCI DSS) compliance is not a one-and-done process, but ongoing and continual.
Yet many merchants and service providers that achieve PCI DSS compliance go on to neglect their information security controls. Soon, they’ve slipped into the danger zone. A 2018 Verizon report found that 47.5 percent—nearly half—of businesses that had achieved PCI compliance had failed to maintain it.
But maintenance is at least half the point of PCI DSS. The PCI Security Standards Council (PCI SSC) states clearly that meeting PCI DSS requirements is not the end goal for information security, but only the beginning.
Becoming PCI compliant doesn’t guarantee that credit card or cardholder data protection. Instead, it means an entity has the essential controls in place to help prevent a data breach and prevent unauthorized access to payment card information.
Maintaining PCI compliance requires constant vigilance. In their quest for personal and payment information, cybercriminals never rest. And neither can you.
Here are some best practices for staying in PCI DSS compliance between yearly audits or self-assessments:
- Make PCI DSS compliance part of your daily security strategy.
- Create a PCI DSS Compliance Manager role, assigning responsibility for ongoing compliance.
- Build a culture of security and risk management in your company.
- Continuously monitor your controls, and respond to failures promptly.
- Run vulnerability scans and penetration tests frequently.
- Train all personnel in security awareness, and update that training frequently.
- Monitor your third-party service providers to ensure they stay in compliance.
- Update your compliance program as new threats emerge.
- Keep an audit trail, documenting everything.
How to Choose PCI Compliance Software
Meeting the 12 requirements and 281 directives of the Payment Card Industry Data Security Standard (PCI DSS) can be onerous and time-consuming—especially if you’re using spreadsheets for compliance management.
Just gathering the documents you need at audit time can be a huge hassle, as well as keeping apprised of new PCI standards, tracking vendor compliance, and continually testing the controls around your cardholder data environment (CDE).
And yet, all these tasks are critical for merchants and service providers to comply with PCI DSS—and comply you must. PCI compliance helps protect clients’ and customers’ credit card and cardholder data from security breaches and enables companies to do business. Non-compliance is not an option if you want to accept payment cards.
Fortunately, PCI DSS compliance solutions can perform many of these tasks for you. But—which software should you use?
The best PCI compliance management software will:
- Probe all areas of your CDE, from payment application to security systems, to ensure that you comply with the PCI DSS requirements
- Integrate a top-quality approved scanning vendor (ASV) (i.e. Qualys, Tenable) and other applications
- Double as audit software, performing unlimited internal audits with a few clicks
- Continually monitor your systems and networks to check your PCI compliance status
- Generate and send vendor surveys, and audit third-party vendor and service provider PCI compliance status, including how well they restrict access to the CDE
- Collect and gather all the documentation you need at audit time
- Provide an easy-to-read centralized dashboard to show PCI compliance gaps as well as where your efforts aid in compliance with other frameworks, for greater efficiency
ZenGRC meets all these criteria and more.
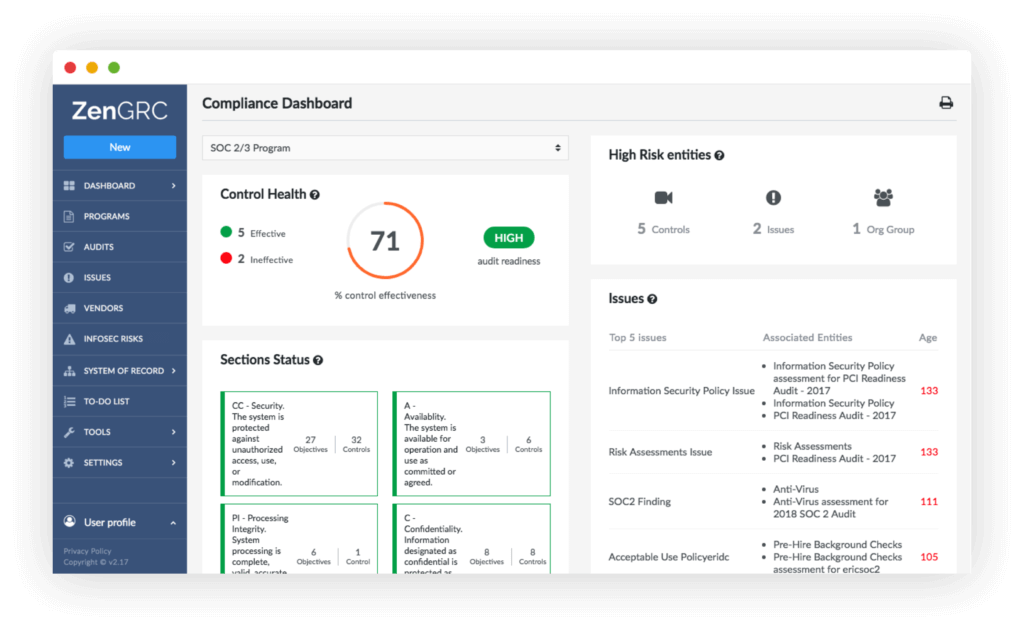
Our state-of-the-art governance, risk, and compliance solution act as the ultimate PCI assessment tool. Zen continuously scrutinizes your networks and systems against the PCI DSS compliance standards to tell you where you fit in—and where you (and your vendors) fall short.
Zen’s color-coded “single source of truth” dashboards show at a glance how to fill compliance gaps, updating automatically as the framework changes. It tests the controls around your CDE and performs internal audits with a few clicks, as often as you desire.
ZenGRC also integrates seamlessly with a variety of software, migrating data automatically so you don’t have to and maps controls to all of your compliance requirements whether they be for PCI, HIPAA, SOC, or otherwise.
Suddenly, PCI DSS compliance just got a lot simpler. With ZenGRC, you can let the software do the compliance heavy lifting, and turn your attention to keeping your customers and clients happy. Minding the store, worry-free: that’s the ZenGRC way.
