
Intro
If you’re a cloud service provider (CSP) wanting lucrative federal contracts—or, these days, contracts with any major client—compliance with the Federal Risk and Authorization Management Program (FedRAMP) is a must.
Aimed at ensuring the security and privacy of the information agencies place into the public cloud, a FedRAMP certification has become the most coveted credential CSPs can obtain.
If getting certified were easy, however, everyone would be doing it. FedRAMP certification is a rigorous, multistep process with—being a federal program—more acronyms than a bowl of alphabet soup and a plethora of documents to complete.
To help simplify your FedRAMP certification, we’ve compiled this guide to all things FedRAMP.
Scroll down to read our series of short articles answering your most pressing FedRAMP questions. They’ll lead you step-by-step down the path to greater cloud security and the enhanced prestige that qualifying for this important and rigorous federal program confers.
Click on the links scattered throughout this guide for a deeper dive into specific topics.
If you want even more help with FedRAMP compliance, contact one of our experts for information on quality software that can do most of the work for you, liberating you from the tyranny of spreadsheets and freeing you to focus on other, more pressing tasks—such as your business and bottom line.
What Is FedRAMP Compliance?
Cloud service providers (CSPs) are in compliance with the Federal Risk and Authorization Management Program (FedRAMP) when they conform to its federal-government-wide standardized requirements for information security assessment, authorization, and continuous monitoring for cloud products and services.
The U.S. government requires FedRAMP program compliance from all who provide cloud computing products and services to federal government agencies.
FedRAMP: A Brief History
The federal Office of Management and Budget announced the establishment of FedRAMP in 2011 “to provide a cost-effective, risk-based approach for the adoption and use of cloud services to Executive departments and agencies.” The memorandum followed a federal “Cloud First” initiative requiring agencies to move their data and workflows to the cloud.
Previously, federal agencies had self-assessed their CSPs’ security using the Federal Information Security Management Act of 2002 (FISMA). FedRAMP has been called “FISMA for the cloud,” and the description fits.
In 2012, the U.S. General Services Administration (GSA) formally launched FedRAMP. The program’s requirements included the use of federally-accredited third-party assessment organizations (3PAOs) to determine whether a CSP complies with FedRAMP.
It also requires every cloud provider holding federal data to obtain an Authorization to Operate (ATO) from the agency it serves, which may occur after the 3PAO assessment and, if necessary, remediation of any findings.
Two Types of ATO
Cloud providers may obtain two types of FedRAMP authorization.
- The Joint Authorization Board (JAB) Provisional authorization (P-ATO) is the most stringent, intended for CSPs wanting to provide cloud services to multiple agencies or even government-wide.
- Agency authorization (ATO) is a bit less complicated, designed for CSPs wanting to serve one or two agencies.
To make this determination, the assessor will measure the CSO’s security controls against those in the applicable National Institute of Standards and Technology (NIST) publications, such as NIST 800-53.
Achieving FedRAMP Compliance: Four Steps
1. DOCUMENT.
The compliance process begins with a CSP’s categorizing the product or service being considered for FedRAMP in accordance with the NIST publication FIPS-199, “Standards for Security Categorization of Federal Information and Information Systems.”
Which category applies to the cloud product or service under consideration—low, moderate, or high—depends on how much damage would likely occur in the event of a security breach, which in turn determines the type of data the provider is authorized to handle. The level chosen determines which NIST 800-53 and FedRAMP controls should be used to comply with the program’s requirements.
The CSP must formulate a plan for implementing the required controls, and document in detail how it does so. The CSP must also develop detailed contingency, incident response, configuration management, and associated plans.
2. ASSESS.
The 3PAO now begins a security assessment plan that spells out the approach for testing the controls that have been put in place. This assessment must be performed on the system to be used, not on a test system or development system.
3. AUTHORIZE.
The federal agency or agencies issuing the ATO review the assessor’s Security Assessment Report and approve it, ask for additional tests, or require remediation of findings before issuing the ATO.
4. CONTINUOUSLY MONITOR.
The CSP monitors its cloud security controls to ensure that they continue to work, and provides periodic results to the authorizing agency. The cloud provider also scans its systems monthly for vulnerabilities in its databases, servers, and applications, and third-party assessors assess the security of the cloud product or service every year.
What Is FedRAMP Certification?
“FedRAMP certification” is a term referring to the Authority to Operate (ATO) that cloud service providers (CSPs) must obtain before they can provide cloud products or services to federal agencies.
Managed by the U.S. government’s General Services Administration (GSA), the Federal Risk and Authorization Management Program, or FedRAMP, spells out information security controls that CSPs must implement to become FedRAMP-compliant, and eligible for federal government contracts.
The FedRAMP program is similar to the Federal Information Security Management Act (FISMA), but it addresses specifically cloud computing security assessment, authorization, and continuous monitoring.
Cloud providers wanting FedRAMP certification must undergo an assessment by a certified third-party assessment organization (3PAO). Using National Institute of Standards and Technology (NIST) controls, an assessment will determine the sensitivity of information that the CSP can securely handle on an agency’s behalf. The rigor of the FedRAMP authorization process will depend partly on which kind of ATO the CSP seeks.
Joint Authorization Board (JAB) Provisional authorization (P-ATO)
Joint Authorization Board (JAB) Provisional authorization (P-ATO) is the most stringent, intended for CSPs wanting to provide cloud services to multiple agencies or even government-wide.
The JAB comprises members of the U.S. Department of Defense, Department of Homeland Security, and the GSA. It evaluates cloud service offerings with the FedRAMP Program Management Office and the CIO Council using a process called FedRAMP Connect.
Only three CSPs are eligible for P-ATO evaluation each quarter; the FedRAMP PMO prioritizes them in part based on how many agencies want to use their services. To streamline the process, CSPs wanting JAB authorization must follow the instructions in the JAB Prioritization Criteria and Guidance document.
After a CSP is prioritized, it has 60 days to become FedRAMP Ready (if it isn’t already). Being prioritized to work with the JAB and being deemed “FedRAMP Ready” by the FedRAMP PMO constitute the first phase of the JAB authorization process. At this point, the CSP will begin working with a third-party assessor.
The ATO issued by the JAB is deemed “provisional” because the federal government itself cannot assume responsibility for any CSP’s security or risk level. Each agency wanting to do business with the cloud provider must, instead, issue its own authorization, attesting that they are accepting the risk that comes with using the CSP’s products and services. However, these agencies do not need to conduct additional security tests.
Agency authorization (ATO)
Agency authorization (ATO), less complicated and less difficult to obtain than the JAB P-ATO, is intended for CSPs wanting to serve just one or two agencies. For this type of authorization, the CSP works directly with the agency or agencies it wants to serve. The agency itself issues the ATO, and the FedRAMP PMO validates the authorization.
An ATO does not require the JAB readiness assessment, but it does require working with a third-party assessor to determine the risk level of the cloud provider or offering as well as taking the following steps:
Preparation and consulting
You will likely need help bringing your system in line with FedRAMP requirements and documenting your efforts.
Assessment
Your 3PAO conducts a technical assessment to determine your compliance with NIST SP 800-53 Revision 4 and FedRAMP controls.
Continuous monitoring
To maintain compliance with FedRAMP, you will need to continuously monitor the system to ensure that the controls you put into place are working and effective.
What Are the FedRAMP Levels?
The Federal Risk and Authorization Management Program (FedRAMP) grants authorizations to cloud service providers (CSPs) and cloud service offerings (CSOs) at three impact levels: low, moderate, and high. These levels refer to the sensitivity of the data the cloud provider is equipped to process, store, and transmit.
A low impact risk rating authorizes a CSP to host data that is intended for public use. Unauthorized access to this data wouldn’t compromise the client’s mission, safety, finances, or reputation.
A moderate impact risk rating allows a CSP to host data that’s not available to the public, such as personally identifiable information. A breach of this data could have a serious impact on an agency’s operations.
p>A high impact risk rating means a cloud provider is secure enough to host sensitive federal information, such as law enforcement, emergency services, and healthcare data. Breaches to government systems containing this data would likely be catastrophic — perhaps shutting down operations, bringing financial ruin, or posing a threat to intellectual property or even human life.
These security levels are defined in the National Institute of Standards and Technology’s (NIST) Federal Information Processing Standard 199 (FIPS 199), “Standards for Security Categorization of Federal Information and Information Systems,” which defines data “security” as protection of information confidentiality, availability, and integrity.
To be assigned a risk level, a CSP or CSO must undergo a security assessment by a certified third-party assessor. The assessor will measure the security controls used by the cloud service or product seeking FedRAMP authorization against those listed in applicable (NIST) publications, such as NIST 800-53.
CSPs use these risk ratings to ensure that their information systems meet the minimum security requirements necessary to process, store, and transmit data for their federal-government customers. Federal agencies choose cloud providers, products, and services according to the level of security they need. For example, an agency that doesn’t handle sensitive government information or PII might use a cloud service with a “low impact” risk level.
Each level of risk requires a minimum number of security controls to ensure that the cloud service or product is secure enough to to safeguard the information it contains. Under FedRAMP, high-level cloud providers, products, or services must comply with 421 controls. For moderate-level CSPs, the number of controls drops to 325, while low-level providers need only implement 125 controls.
Controls are the technologies and techniques CSPs use to secure the federal information they store in the cloud.
FedRAMP released the high-level security baseline in June 2016. Previously, federal agencies could outsource only low-level and moderate-level information and workloads to CSPs. Now, federal agencies can store highly sensitive data with any high-level cloud services provider that’s FedRAMP compliant.
FedRAMP’s Joint Authorization Board, comprising chief information officers from the U.S. Department of Defense (DoD), the U.S. Department of Homeland Security (DHS), and the General Services Administration (GSA), develops FedRAMP accreditation standards and reviews FedRAMP authorizations.
How Much Does It Cost to Get FedRAMP Certified?
Compliance with FedRAMP, the government program to certify the security of cloud-based technology providers bidding on government contracts, isn’t cheap. Certification costs for cloud service providers (CSPs) used by federal agencies can range from several hundred thousand dollars to more than $1 million, depending on the complexity and security posture of your cloud computing service.
What Factors Influence the Cost of FedRAMP Certification?
Numerous factors can affect the cost of FedRAMP compliance. Among them:
- Scope: How many services are you seeking to authorize for federal government use? How complex are these services?
- Approach: Are you seeking an agency Authorization to Operate (agency ATO) or the more sweeping Joint Authorization Board Provisional Authorization to Operate (JAB P-ATO)? The latter is overseen by the Department of Defense (DoD), General Services Administration, and Department of Homeland Security. It requires a pre-authorization readiness assessment, which adds time and expense to the process. The FedRAMP Accelerated program, instituted in 2016, is designed to cut those costs and the time it takes to obtain a P-ATO to six months or less.
- Risk level: FedRAMP divides the data being processed into three impact levels. These categorizations are based on whether the federal information you process requires low, moderate, or high security. The higher the level, the more controls you will need to implement and the more rigorous your third-party assessment organization’s (3PAO) security assessment will need to be. These assessments typically run $150,000 to $200,000, including the baseline readiness assessment – not required for an ATO, but highly recommended.
- Current information security maturity: How secure are your cloud solutions today? How up-to-date is your cybersecurity program? Are you already compliant with other frameworks such as FISMA or NIST? The JAB review of your readiness assessment may require you to remediate any vulnerabilities and alter your existing cloud security controls before working with government agencies. Additional development and engineering needed to become “FedRAMP Ready” can comprise 50 percent of certification costs.
- Resources: Do you have staff qualified to steer your organization through the authorization process? Consultant costs can run $20,000 to $40,000 short-term, and much more if you need help throughout the process of becoming FedRAMP compliant.
What Are Other Capital Expenditures for FedRAMP Certification?
Your FedRAMP certification will come with other costs that you may not have considered. For instance, the assessor reviewing your case will require extensive documentation of your existing information systems and controls. Compiling this documentation can cost as much as $400,000.
FedRAMP authorization also requires continuous monitoring of your security plan to remain in compliance; even if you’re able to handle this work in house it can become expensive quickly. Finally, FedRAMP compliance requires an annual recertification. While not as costly as your initial investment, this procedure can still cost up to $200,000 dollars. It’s critical that your company consider all of the potential costs up front so you can avoid being overwhelmed and over budget during this process.
Average FedRAMP Accreditation Costs
With so many factors in play it’s impossible to give a precise estimate of how much FedRAMP accreditation for your cloud service offerings will cost. On average you can anticipate costs of $200,000 to $700,000 depending on the factors listed above.
You can streamline this process and decrease costs by preparing before you begin the accreditation process. Make sure you thoroughly understand what the U.S. government security requirements are and strive to align to the appropriate security standards before you seek FedRAMP accreditation.
Why Does My Business Need FedRAMP Certification?
If you’re a cloud service provider (CSP) wanting to do business with the federal government or federal agencies, you need FedRAMP certification. Without a FedRAMP Authorization to Operate (ATO), cloud providers aren’t eligible for federal contracts.
The high costs of FedRAMP authorization and audits may make you wonder if the return on investment is worth the expense. But a single ATO can unlock your ability to serve multiple agencies, which could be lucrative—increasingly so, with time.
The U.S. government’s “Cloud First” initiative means more and more agencies are moving their data and workflows to the cloud—which means more business for FedRAMP-certified CSPs.
And FedRAMP’s “do once, use many times” approach to certification means that, once you obtain one ATO, you have ongoing authorization to serve any agency processing data at your assigned risk level. For instance, if you have an ATO in the “moderate” category, you’re automatically eligible for contracts with other agencies wanting to move moderate-level data to the cloud.
What if you don’t intend to pursue federal contracts? You can still benefit from being FedRAMP compliant.
Having the cloud information security controls that FedRAMP requires tells customers that your cloud offering—be it hosting, software-as-a-service (SaaS), or something else—is secure. Being able to advertise your adherence to FedRAMP controls says you’re serious about security, and can give you a competitive edge with non-government customers, as well.
What Is a FedRAMP Readiness Assessment?
A FedRAMP readiness assessment is a certified third-party assessment organization’s (3PAO) consideration of whether a cloud service provider (CSP) or cloud service offering (CSO) can meet FedRAMP requirements. This assessment occurs before the FedRAMP authorization process begins, and is intended to streamline that process.
To determine whether you are “FedRAMP Ready,” the 3PAO will measure your cybersecurity controls against those required by the National Institute of Standards and Technology (NIST). These controls include regular penetration testing, continuous monitoring, multi-factor authentication, and the ability to segregate systems containing federal agencies’ data from the rest of the cloud environment.
After completing the assessment, the 3PAO will issue a Readiness Assessment Report for the JAB and FedRAMP Project Management Office to review.
Only CSPs pursuing a Joint Authorization Board Provisional Authorization to Operate (JAB P-ATO) are required to have a RAR. But even those wanting the more-limited ATO may still wish to establish themselves as “FedRAMP Ready.”
Cloud providers with that designation appear in the FedRAMP Marketplace, a list of CSPs from which agencies may choose.
How Do I Become FedRAMP Ready?
Passing a FedRAMP Readiness Assessment isn’t easy. The pre-authorization review of cloud service providers (CSPs) or offerings is quite rigorous, in fact—not as challenging as the full FedRAMP certification assessment, but a complex process nonetheless.
The certified third-party assessment organization (3PAO) you engage to conduct the assessment will be checking the security of your cloud environment or of the product or service for which you are seeking a Joint Authorization Board Provisional Authorization to Operate (JAB P-ATO) or federal agency Authorization to Operate (ATO).
Being FedRAMP Ready is a P-ATO requirement only. However, it’s recommended for those seeking an ATO, as well, or even if you’re just thinking about pursuing FedRAMP authorization. The resulting Readiness Assessment Report (RAR) can serve as a self-assessment showing deficiencies in your security and what you must do to correct them.
The readiness assessment process differs quite a bit from the P-ATO or ATO assessment, however.
To obtain an ATO or P-ATO, for example, you’ll need to present documentation showing that you comply with all 17 FedRAMP control families—your System Security Plan SSP). To be certified as FedRAMP Ready, you need only present your policies and procedures pertaining to your system security. However, you should have started your SSP.
Where To Start
Your 3PAO will not only rely on your documentation when assessing your FedRAMP readiness. They will also visit your enterprise at least once to interview your technical and security teams. Advance preparation is a must.
When preparing for your readiness assessment, you may wish to conduct a self-assessment, focusing your efforts on five key areas:
- Federal Requirement Mandates: To pass the readiness test, you must meet these mandates:
- Use FIPS 140-2-validated or National Security Agency (NSA)-approved cryptographic modules.
- Fully support user authentication via Agency Common Access Card (CAC) or Personal Identity Verification (PIV) credentials
- Operate your systems at eAuth Level 3 or higher. This means that there is high confidence that the identity being authenticated is valid.
- Be able to remediate high-level vulnerabilities within 30 days and moderate-level vulnerabilities within 90 days
- Meet Federal Records Management Requirements including the ability to support record holds, National Archives and Records Administration (NARA) requirements and Freedom of Information Act (FOIA) requirements
- Boundary definition: You must fully understand your system boundary and its components within and without. The 3PAO will conduct discovery scans to validate the system boundary.
- Data flow diagrams: You must be able to accurately define how federal data flows into, through, and out of the system so the appropriate security controls can safeguard the data during processing, transmission, and storage.
- Multifactor authentication (MFA): You must use MFA for privileged accounts, and it should be enabled for all system users.
- Segregation/isolation of users and data: You must be able to show that you have isolated the systems containing federal data and their users. Access to these segregated systems as well as the flow of federal data must be restricted, as well.
It’s also wise to review FedRAMP’s Security Assessment Framework and familiarize yourself with the four process areas: Document, Assess, Authorize, and Monitor—the latter involves continuous monitoring of the availability, confidentiality, and integrity of your systems.
Once you have been deemed FedRAMP Ready, your service will get a FedRAMP Marketplace listing and be visible to federal agencies selecting a cloud provider, product or service.
How Long Does a FedRAMP Readiness Assessment Take?
According to the FedRAMP Project Management Office (PMO), a FedRAMP Readiness Assessment should take two to four weeks to complete for a “mid-size, straightforward system.” About half that time will be devoted to testing and information gathering, with the rest comprising analysis of the results and report writing.
If you have to remediate deficiencies that the assessor finds in your system, the time to readiness may be longer. Remediation time can add to the readiness assessment timeline.
If the third-party assessment organization (3PAO) assessing your FedRAMP readiness finds security gaps—a common occurrence—you’ll need to correct those deficiencies before proceeding with your Authority to Operate assessment. Once the 3PAO has determined that you’ve satisfied the readiness requirements, it will submit the FedRAMP Readiness Assessment Report (RAR) to the FedRAMP Project Management Office (PMO), and your CSP or cloud offering will be listed in the Federal Marketplace for other agencies to consider.
FedRAMP Checklist: How to Get FedRAMP Certified
FedRAMP has 17 control families covering everything from access to systems and data integrity. To obtain your FedRAMP Authority to Operate (ATO), you’ll want to familiarize yourself with them, perhaps by perusing our handy FedRAMP audit guide.
The Reciprocity guide, “Preparing for a PCI DSS Audit: Five Steps to Success,” provides helpful tips and tricks for identifying and minimizing your organization’s PCI DSS audit or self-assessment scope, and reaching PCI compliance with relative ease. Download your copy now, and be ready at audit time.

Preparing for a FedRAMP Audit: A Step-by-Step Guide
To get you started on the road to certification, we’ve also compiled this checklist summarizing the most important components of FedRAMP compliance.
- Continuous monitoring
- Remediate all vulnerabilities found in your continuous monitoring program
- Align monthly monitoring scans and your Plan of Action & Milestones (POA&M) to sync with y our patch management program so that you are being notified only of vulnerabilities not already scheduled for remediation
- Security controls
- Review your security controls for commonly overlooked or insufficiently answered problems
- Identify:
- All system components requiring configuration management
- People responsible for configuration
- How the responsible party configures
- Additional FedRAMP requirements
- Where the documentation of these actions is located
- Common problems include:
- Failing to identify portals
- Lacking multifactor authentication
- Failing to segregate/isolate federal systems and customers
- Detection of high vulnerabilities during testing
- Having unclear authorization boundaries
- Having incomplete or poorly defined policies and procedures
- General program
- Communicate with your FedRAMP Information System Security Officer or government liaison.
- Use NIST SP 800-53 Revision 1 Contingency Planning Guide for Federal Information System Appendix B to create a Business Impact Analysis
- If you are a moderate-impact cloud service provider (CSP) and want to want to contract with law enforcement, emergency services, financial services, healthcare, or other high-impact category, use the FedRAMP Categorization Change Form Template
- Readiness Assessment Report (RAR)
- When submitting a RAR, RAR update, or authorization package, notify info@fedramp.gov to ensure review.
- Security Assessment Plan (SAP) & Security Assessment Report (SAR)
- Your third-party assessment organization assessor (3PAO) will conduct vulnerability scans, which includes a review of configuration tools.
- Make sure that your penetration testing tools are in your SAP, and that they match the specifications listed in your Penetration Test Plan document
- Document any false positives or corrected findings with specific items of evidence such as screenshots or scan files, list them by file name, and include the documentation in the SAR
- Assign unique vulnerability identifiers and ensure that previously documented vulnerabilities are not assigned new identifiers
- System Security Plan (SSP)
- Formulate security requirements for each control, including
- A description of the solution
- How the solution meets security control requirements
- Who is responsible for each control
- How often the SSP gets reviewed and by whom
- What triggers reviews
- How reviews will be documented
- What constitutes proof of review
- Policies referenced
- Review security procedures to include all steps for users, system operations personnel, and others.
- Formulate security requirements for each control, including
FISMA and FedRAMP: What's the Difference?
How FISMA Works
FISMA imposes strict information security requirements on all federal agencies and for state agencies and private organizations that work with the federal government.
Enacted in 2002, FISMA mandates a process to strengthen government information systems’ security using the controls in the National Institute of Standards and Technology’s (NIST) Special Publication (SP) 800-53, Recommended Security Controls for Federal Information Systems.
As with FedRAMP, FISMA-compliant organizations receive an authorization to operate (ATO) from the federal agency with which they do business. The agency granting the ATO may perform the contractor’s security assessment, or a certified third-party security assessor (3PAO) may do so.
Unlike with FedRAMP, a FISMA ATO authorizes a business to work only with the agency that issued the ATO. A contractor working with multiple government agencies must attain an ATO from each.
How FedRAMP Works
The Federal Risk and Authorization Program (FedRAMP) is not a law, but a program designed to help federal agencies secure their data and workflows in the cloud, and to streamline the process of choosing and using cloud service providers (CSPs). FedRAMP uses the same NIST security controls that FISMA uses, and so is often referred to as “FISMA for the cloud.”
But FedRAMP focuses exclusively on the security of public cloud environments. Like FISMA, it assigns levels of risk to the systems under its purview—low, moderate, and high—and requires an independent security assessment from a certified third-party assessment organization (3PAO).
The federal government has a “Cloud First” policy that encourages agencies to move their operations to the cloud. FedRAMP helps to make this process less onerous. Its “do once, use many times” framework allows other agencies wanting to work with an authorized CSP to use the authorization package the authorizing agency established to issue its own ATO.
FedRAMP also allows a CSP to obtain a provisional ATO (P-ATO) from the FedRAMP Joint Authorization Board (JAB). The P-ATO verifies that a CSP meets the requirements to securely process, store, and transmit federal data at the risk level assigned. Because the authorization is government-wide, agencies can issue an ATO to the cloud provider without conducting further security tests.
FedRAMP also requires CSPs to conduct continuous monitoring of their systems, services, and cloud products to remain in compliance.
NIST and FedRAMP: What's the Difference?
If FedRAMP is a recipe for cloud information security, NIST provides the ingredients.
The National Institute of Standards and Technology (NIST) is a federal agency that creates information security standards, or controls, for the federal government. It publishes its standards in documents such as NIST SP 800-53, Recommended Security Controls for Federal Information Systems. The government requires federal agencies to comply with NIST standards and guidelines within one year after they are published.
A number of federal laws and programs, including the Federal Information Security Management Act of 2002 (FISMA), which in 2014 became the Federal Information Modernization Act; the Health Information Portability and Accountability Act (HIPAA), and the Federal Risk and Authorization Management Program (FedRAMP) use NIST SP 800-53 security controls as a basis for determining whether the cybersecurity measures in place are rigorous enough.
FedRAMP assessors use NIST SP 800-53 when performing a security assessment on a cloud service provider (CSP). They measure the controls used in the CSP’s environment or that of a product or service to determine whether it meets requirements for an agency-issued authorization to operate (ATO).
— Is Amazon Web Services FedRAMP Certified?
One of the world’s largest cloud service providers (CSP), AWS serves more than 2,000 government agencies, including the U.S. Department of Defense (DoD), and third-party vendors to federal agencies. Amazon’s FedRAMP-certified offerings are
- AWS GovCloud, created specifically for government agencies and their third-party vendors. GovCloud has a FedRAMP Joint Authorization Board (JAB) Provisional Authorization to Operate (P-ATO) and multiple agency authorizations (ATO) at a “high” impact level. Its server is located in the northeastern U.S.
- AWS East-West, for all cloud service providers including government agencies. AWS East-West has a JAB P-ATO and multiple agency authorizations at the “moderate” impact level. Its server is in the Northwest U.S.
These cloud systems have been granted authorizations to operate, have properly applied National Institute of Standards and Technologies (NIST) security controls, have passed a security assessment by an accredited, independent third-party assessor (3PAO), and conduct the continuous monitoring that the FedRAMP program requires. They are compliant with the Federal Information Systems Modernization Act (FISMA), as well.
What Does FedRAMP Penetration Testing Entail?
Every cloud service provider (CSP) must have network penetration testing to qualify for a “high” or ”moderate” authorization to operate (ATO) from the Federal Risk and Authorization Management Program (FedRAMP).
FedRAMP requires third-party assessment organizations (3PAOs) to conduct three kinds of tests on a CSP or the cloud product or service for which it seeks an ATO:
Penetration test
Vulnerability scan
Security controls test
What is Penetration Testing?
Penetration testing is a standard cybersecurity test that involves attacking IT systems to expose their weaknesses. Its object is to determine where and how a cybercriminal might enter your network and gain access to the information there. Penetration testing is not the same as vulnerability testing. Your 3PAO will conduct penetration tests manually, while vulnerability scans are automated.
FedRAMP ‘Pen Test’ Requirements
FedRAMP requires penetration testing as part of the initial security assessment for all systems pursuing a “moderate” or “high” FedRAMP authorization, as well as for annual assessments.
The tests must conform to the standards contained in the FedRAMP Penetration Test Guidance Document, which identifies attack vectors to include, and requirements for reporting test results. These requirements are based on those defined by the federal General Services Administration (GSA), National Institute of Standards and Technology (NIST) and Federal Information Processing Standards (FIPS).
FedRAMP penetration testing best practices include:
- Set a proper scope. Your penetration test must probe the area for which you are seeking an ATO. If the scope is too small, the testing may be invalid. If the scope is too large, the test team may inadvertently infiltrate a system for which they do not have authorization. Your Penetration Test Plan should identify the scope of your pen test.
- Know that underlying providers are out of scope. If your SaaS system resides on a FedRAMP-authorized PaaS or IaaS, only your SaaS components are within scope. There’s no need to perform a pen test on the underlying PaaS or IaaS.
- Be aware of your underlying providers’ requirements. If your SaaS system resides on an underlying PaaS or IaaS, you may need to notify the provider before penetration testing or scanning.
- Make your reporting comprehensive. You must document your penetration test activities and results in a comprehensive Penetration Test Report (PTR). The PTR includes the tests performed and the results of those tests, the access paths utilized, and test findings and evidence.
- Address all FedRAMP-identified attack vectors. The FedRAMP PMO sometimes sees vulnerability scans represented as penetration testing. The two are not synonymous. FedRAMP-acceptable penetration tests must include internal, external, and lateral movement attack testing, from trusted and untrusted actors. It should include attempted exploitation of any web applications, mobile applications, and the system’s network within the system’s boundary. For multitenant systems, penetration testing must include a trusted tenant attempting to cross tenant boundaries.
- Configure non-production test environments exactly the same as the production environment. Penetration testing in a production environment is not always feasible or tenable for a variety of reasons, so FedRAMP allows the use of a test environment configured to mirror exactly the production environment. Similar or like environments do not suffice. Tenant-to-tenant testing is a good use case for penetration testing in a non-production environment.
- Include a phishing test in your social engineering test. At a minimum, send the phishing email to all CSP staff with logical access to the system. Do not warn staff of the phishing test.
How to Automate Your FedRAMP Compliance
Cloud service providers wanting to do business with the federal government need an authorization to operate (ATO) or provisional authorization to operate (P-ATO) under the Federal Risk and Authorization Management Program (FedRAMP). This is much easier said than done, however—especially if you’re using old-fashioned spreadsheets to keep track of compliance tasks.
From the initial security assessment to procure your ATO to the ongoing continuous monitoring required to maintain it, the U.S. government wants proof that your CSP takes cybersecurity seriously if you’re going to process, store, or transmit government agencies’ data. The authorization process could take many months to complete—but for lucrative government contracts, it’s worth the effort, right?
The good news is, FedRAMP compliance doesn’t have to be that hard. Modern tools designed to automate the process can do much of the work for you—and a good one like Reciprocity’s ZenGRC software-as-a-service (SaaS) can help you double-up compliance with other regulatory and industry frameworks and standards, including NIST SP 800-53, at the same time.
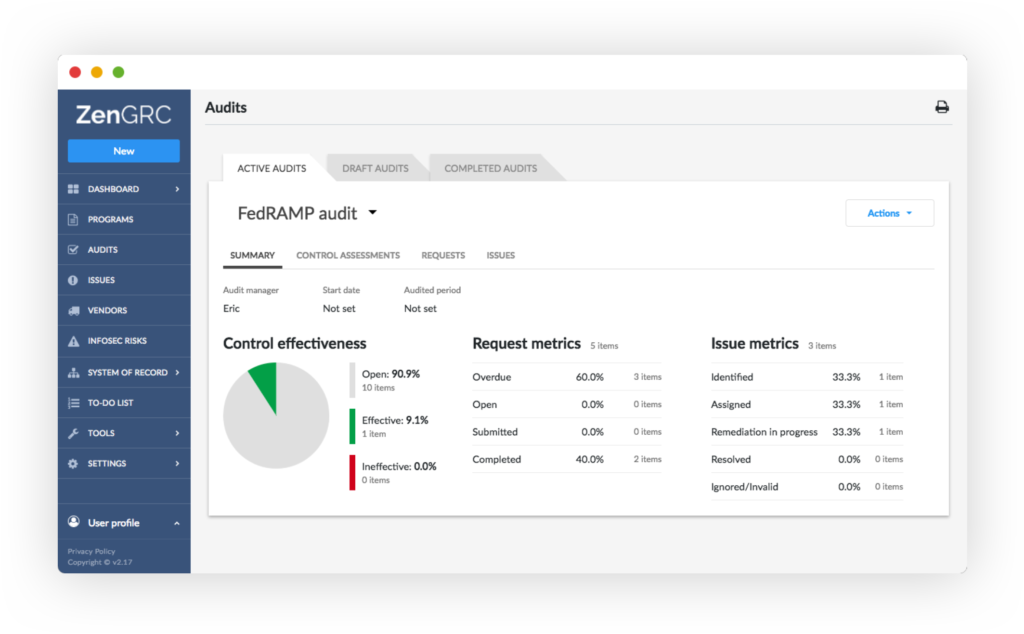
ZenGRC automates the entire FedRAMP compliance process. It
- Probes your organization’s systems for FedRAMP conformity and alerts you when it finds a flaw
- Makes detailed, prescriptive suggestions for correcting compliance gaps
- Summarizes, in real time, your risk and compliance posture, and helps you prepare for penetration testing and other tests required by FedRAMP
- Helps prepare you for FedRAMP Readiness with unlimited, in-a-click self audits
- Creates, gathers, and stores documentation of your compliance actions in a “Single Source of Truth” repository for your 3PAO to view
- Continuously monitors your systems to ensure that you maintain your FedRAMP authorization between audits, and alerts you in real time to issues and vulnerabilities
- Automatically monitors your third-party-vendors, makes it easy to generate and send vendor surveys, and compiles results automatically
- Provides an in-a-glance view of your overall compliance posture on user-friendly, color-coded dashboards
With ZenGRC performing so many FedRAMP-compliance tasks for you and, at the same time, helping to improve your cloud security, you can stop worrying about obtaining and maintaining your coveted FedRAMP ATO or P-ATO.
