
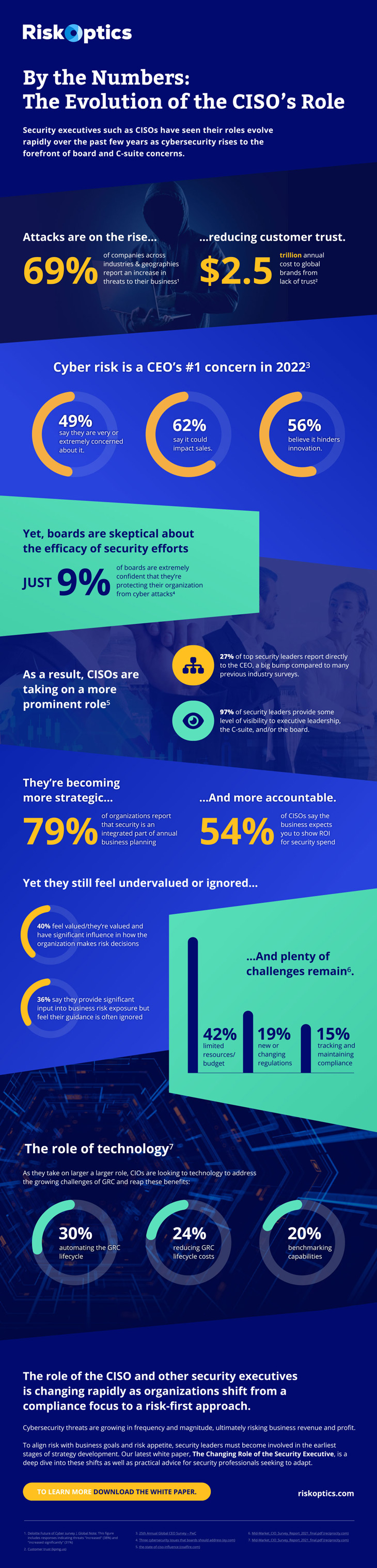
Security executives such as CISOs have seen their roles evolve rapidly over the past few years as cybersecurity rises to the forefront of board and C-suite concerns.
Are you ready to keep up?
Share this Infographic on Your Site
As organizations shift from a compliance focus to a risk-first approach. Cybersecurity threats are growing in frequency and magnitude, ultimately risking business revenue and profit.
To align risk with business goals and risk appetite, security leaders must become involved in the earliest stages of strategy development. Our latest white paper, The Changing Role of the Security Executive, is a deep dive into these shifts and practical advice for security professionals seeking to adapt.
Download the white paper to learn more about the changing role of security executives.
What is CISO in Cyber Security?
A Chief Information Security Officer (CISO) is a senior executive who is part of the “C-suite” and is responsible for establishing and implementing an information security program that safeguards an organization’s data and systems. CISOs manage risk management and ensure the organization’s security posture aligns with its business objectives.
CISOs collaborate closely with other high-ranking managers, such as the Chief Information Officer (CIO) and Chief Technology Officer (CTO), to guarantee the effectiveness and efficiency of the organization’s security program. trusted CISOs are often educated in information security, computer science, computer engineering, or a similar discipline.
To be a successful CISO, you must have a thorough awareness of security technology and procedures, as well as a solid understanding of business and risk management. There needs to be more than just understanding the security aspect. Most importantly, a successful CISO must be able to:
- Communicate well with both technical and non-technical people.
- Explain the organization’s security position to top management (especially if the situation is not suitable).
The History of the CISO Role
The CISO job dates back to the late 1990s when corporations realized the need to protect their digital assets. The potential risks connected with cybersecurity threats grew with the rising internet usage and digital technology.
Organizations formed jobs devoted to information security management in response to these concerns. These positions were formerly known as Information Security Managers (ISMs) and were frequently associated with the IT department. They were in charge of guaranteeing the organization’s information’s secrecy, integrity, and availability.
As the ISM’s function expanded to cover broader obligations such as risk management and compliance assurance, the title was changed to Chief Information Security Officer (CISO), reflecting the growing prominence of the post and the expanding responsibilities that came with it.
Since its beginning, the CISO’s job has changed dramatically. Initially, the CISO was in charge of technical elements of information security, such as installing firewalls, intrusion detection systems, and other security technologies. However, as cyber risks evolved, the CISO’s responsibilities extended to encompass risk management, compliance, and incident response.
The CISO now plays a crucial part in an organization’s success. They are in charge of ensuring that an organization’s information is safe, complies with applicable standards, and is appropriately prepared for and capable of responding to cyber events.
Key Responsibilities of a CISO
A CISO oversees an organization’s information system’s overall security. This includes the following:
- Creating and executing security rules and processes, sometimes with the assistance of a security framework
- Managing security personnel, which includes supervising many security teams in more prominent companies
- Recognizing network activity and anticipating possible risks
- Overseeing incident reaction and recovery planning
- Coordination of reaction and recovery operations in the event of a data or security breach
- Reporting to a defined hierarchy, which might include the CIO, CEO, or even the board of directors
The Three CISO Personality Types
While no CISO can be characterized solely as one kind, these classifications guide where the CISO should report.
The Technical Information Security Officer (TISO)
The TISO specializes in managing technical security challenges, security operations, and monitoring duties such as managing firewalls and IDS/IPS infrastructure, among other things. The TISO is also in charge of coordinating and managing technical policy, control, and assessment operations. This person should report to the CIO, CTO, or IT management.
The Business Information Security Officer (BISO)
The BISO focuses on business-related information security challenges, such as safely adopting customer-facing technology and protecting customer information effectively.
The BISO’s primary goal is to ensure that the business unit or division knows that information security is a business imperative, just like any other. This person also helps implement and translate enterprise security needs, policies, and procedures.
Furthermore, this professional should conduct self-assessments or, at the very least, coordinate discovered business-related security vulnerabilities. A BISO should ideally be incorporated in each significant business unit or division. BISOs must report to upper management.
The Strategic Information Security Officer (SISO)
The SISO specializes in converting high-level business needs into enterprise security initiatives and programs that must be implemented to accomplish the firm’s purpose, goals, and objectives.
The SISO must coordinate with the OPSO and BISO functions to guarantee proper progress and traction. The SISO should also be in charge of metrics, dashboards, executive reports, and evaluations of the enterprise’s State-of-Security (SOS) to the Board of Directors.
The SISO should report to an executive management function or committee, such as the CRO, COO, Chief Legal Counsel, or Chief Operating Officer. One factor to evaluate in the reporting relationship is whether the executive can adequately assist the SISO.
Can I Hire a CISO?
Hiring a CISO is critical for any business that deals with sensitive information, such as banks, healthcare companies, and government agencies. The cost of a data breach may be enormous financially and in terms of reputational harm to the firm.
However, recruiting and retaining your in-house CISO on the payroll may not always be achievable for various reasons. Hiring a CISO from an outside business might be more cost-effective in some situations, such as when:
- Your company is small or medium-sized, and a cost-effective alternative to recruiting is appreciated.
- You may require a security expert for a limited time, such as for a specific project or for forthcoming audits and compliance engagements.
- You may be looking for your own professional to recruit and need someone to tide you over in the interim.
- You don’t want to be without an IT security professional because they are on vacation or prolonged leave.
Maintain Compliance and Certifications with ZenGRC
Whatever your compliance concerns are, data and cybersecurity must be integrated into all elements of your organization.
Instead of utilizing spreadsheets to manage your compliance needs, use ZenGRC to automate documentation and audit management across all your compliance frameworks. The compliance, risk, and workflow management software from ZenGRC is intuitive.
ZenGRC includes a variety of compliance frameworks and standards for easy implementation, including PCI, HIPAA, and SOC.
A team of GRC professionals with ZenGRC is constantly at your disposal. One-to-many control mapping simplifies mapping internal controls to various standards so that you may manage PCI DSS compliance alongside other frameworks, making compliance management more accessible than before.
ZenGRC also acts as a single point of truth, ensuring your organization is constantly compliant and audit-ready. Policies and procedures are versioned and easily accessible in the document repository. Workflow management tools include simple monitoring, automatic reminders, and audit trails. Insightful data and dashboards highlight gaps and high-risk areas.
Request a Demo to explore how ZenGRC can help you with compliance and risk management.
1 Deloitte Future of Cyber survey | Global Note: This figure includes responses indicating threats “increased” (38%) and “increased significantly” (31%)
3 25th Annual Global CEO Survey – PwC
4 Three cybersecurity issues that boards should address (ey.com)
5 the-state-of-ciso-influence (coalfire.com)
6 Mid-Market_CIO_Survey_Report_2021_final.pdf (info.archive.zengrc.com)
7 Mid-Market_CIO_Survey_Report_2021_final.pdf (info.archive.zengrc.com)




